From IC Insider HashiCorp
Authors: Greg Thomas, Sr. Systems Engineer, Public Sector
Timothy J. Olson, Systems Engineer, Public Sector
How to Log in without a Virtual Private Network (VPN), Public IP address, or an SSH connection to any target machine.
Digital warfare has early adopters, fast followers, and those left behind. Back in 1996, a Microsoft employee developed the PPTP. “The protocol created a more secure private connection between a user device and the internet” (Techtarget). Since then, virtual private networks (VPNs) have been the most widely accepted and deployed solution for secure user access. Like most technologies, something better always comes along to replace or augment mainstream tooling.
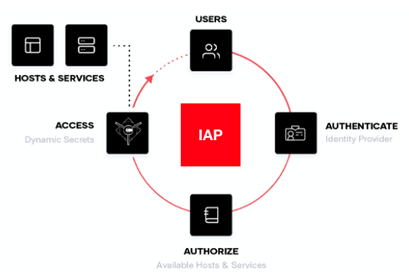
First there were privileged access management (PAM) tools and jump hosts/bastion hosts. We’ve now moved even further beyond those tools which were built in the age of the castle-and-moat datacenter and firewall. Google has been forward-thinking in this regard, with Beyond Corp and the Identity-Aware Proxy (IAP), which enables key capabilities to strengthen user based security posture.
- Control access to your cloud-based and on-premises applications and VMs
- Verify user identity and use context to determine if a user should be granted access
- Work from untrusted networks without the use of a VPN
- Implement a zero-trust access model
Today, with the emergence of a multi-cloud reality (Commercial Cloud Enterprise (C2E)) and ephemeral infrastructure, enterprises, governments, and developers have a significant need for a multi-cloud IAP, going beyond just a single-cloud solution. The challenges faced with securing and controlling access to an enterprise data center as well as a single cloud (C2S) is difficult and now with the era of hybrid cloud environments (C2E) it’s not only essential it’s increasingly complex and challenging. For additional information on overall approaches and considerations for Securing hybrid cloud environments please refer to A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community (IC News, August 14, 2022).
With C2E, the IC is currently undergoing initiatives to adopt effective digital transformation practices. This means adopting industrialized workflows that can securely deliver new business and mission objectives quickly, on demand, and at a very large scale across any operational environment (see IC News, July 6, 2022): A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community). This makes establishing effective and secure zero trust based user access critical and time sensitive. Governance/Security is one of the four key challenges (Skills gap, Scalability, Governance, and Untenable Costs) discussed in a previous article, A Leadership Guide – Multi-Cloud Success for the Intelligence Community (IC News, April 18, 2022).
As hybrid/multi-cloud adoption grows, organizations need a consistent workflow and control point that allows users to access systems without the knowledge of credentials or public Internet Protocol (IP) addresses. This platform agnostic approach will decouple user access from traditional IP centric methods which will increase security posture, flexibility, and efficiency while simplifying user access and reducing cost and risk. As with technological shifts a few early adopters have already shifted to IAP. This article will delve into IAP adoption and how to future proof for the next significant decade-long paradigm shift.
What Is an Identity Aware Proxy?
IAPs provide secure access to users based on authentication and authorization. Essentially they’re tools for human users to remotely access any sort of infrastructure asset. VPNs and jump hosts were built with this in mind, but the difference is that they have limited capabilities to restrict what users can access once they’re on the network. This means that an adversary that has access to a network via VPN or jump host is more likely to find a way to move laterally throughout the network (for additional information on how to prevent Lateral Movement please refer to our previous IC News article, How to Prevent Lateral Movement (Is the “Bad Actor” Already Inside?)).
IAPs, by contrast, have more options for configuring fine-grained, least-privileged access to infrastructure resources, and the user never gains access to networks or other sensitive areas. This is all done by decoupling from traditional network centric approaches and centering the security posture on user identity. Centralizing identity allows authorization across any runtime or platform seamlessly and helps your infrastructure adhere to the principles of zero trust. (also refer to the February 2021 the National Security Agency published, “Embracing a Zero Trust Security Model.”).
Why Not Use a (VPN) or SSH?
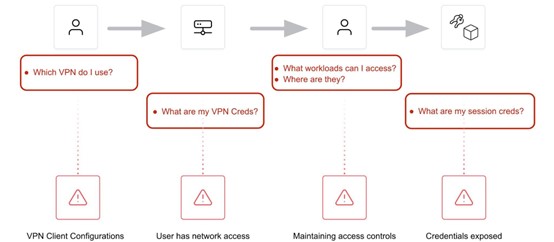
Image Source: Luke McCleary, HashiCorp
Historically, we have used VPN or SSH keys to access private networks and systems. Both methods rely on credentials and static or public IP addresses. These traditional approaches are increasingly risky and open to exposure and compromise as long-lived credentials and static IP addresses are vulnerable to attack. This necessitates adoption of an identity based security approach with a zero trust environment, where temporary or dynamic credentials and being identity-aware is essential.
Users should never possess or know where a VPN or SSH credential is, nor should they care. Allowing the user to maintain credentials or have exposure to or knowledge of the network does not follow zero-trust principles. More and more, users also want their experience to be seamless and allow the same workflow on any system from anywhere, based solely on their identity.
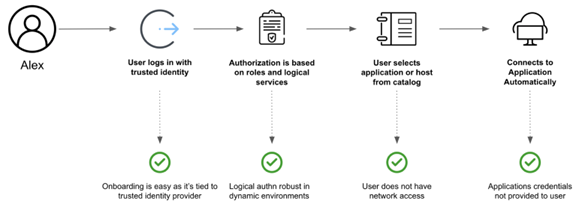
Identity Based Secure User Access Workflow: HashiCorp
Ephemeral Access Models Based on Identity
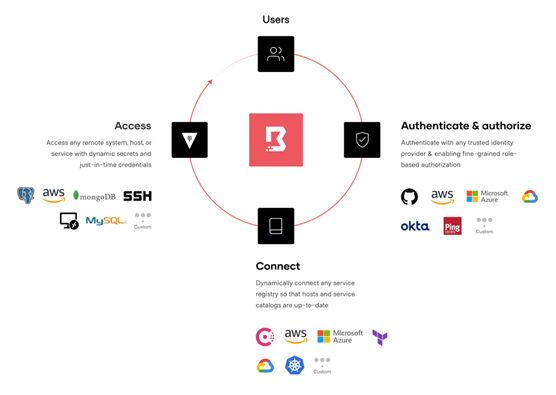
Ephemeral access models based on trusted identity ensure the right roles gain access to the right services. Let’s look at an example of an open-source IAP/secure remote access tool: HashiCorp Boundary.

Image Source: HashiCorp
HashiCorp Boundary is a tool for managing identity-based access for modern, dynamic infrastructure. Boundary’s workflow layers security controls and integrations on multiple levels monitoring and managing user access through
- Tightly scoped identity-based permissions
- “Just-in-time” network and credential access for sessions via HashiCorp Vault
- Single sign-on to target services and applications via external identity providers
- Access-as-code to automate the configuration of user permissions
- Automated discovery of target systems
- Session monitoring and management for access created via Boundary.
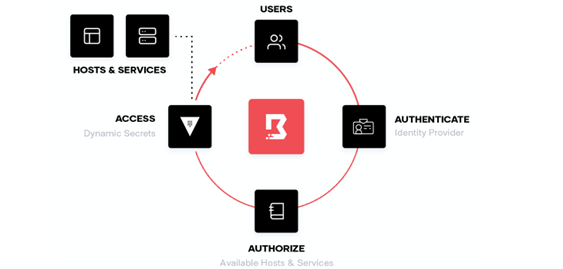
Boundary’s foundation is based on the following important concepts.
- Zero Trust Security: Zero-Trust is an identity-based access model where the user access is continuously authenticated. Access is only authorized when the established rules and policies tied to the user’s identity are verified.
- Consistent Workflow for Access: Once the user is verified and granted access, Boundary securely connects the user to their infrastructure regardless of cloud platform, target environment, or identity provider. This foundation provides continuous user authentication and authorization workflows within ephemeral sessions, which administrators can monitor and manage securely.
- Extensibility with the Ecosystem: Modern organizations often require a multilayered access matrix constructed of identity providers, policy engines, secrets management tools, target types, and cloud providers that integrate and allow users to reside within access workflows requiring vendor lock-in.
Boundary provides a single workflow that allows users, engineers, and developers to access a preassigned target system (VM, database, application, etc.) from their local environment. Boundary integrates with another platform agnostic security tool, HashiCorp Vault, to manage and broker static and dynamic secrets (sensitive information generated on demand, which is unique to a client (user, machine/device, VM, container/Pod, application, etc.), time-based access credentials which are dynamically based on policies and revoke access when the lease expires) to HashiCorp Boundary clients via command line interface (CLI), application programmable interface (API), or desktop clients to create Boundary sessions.
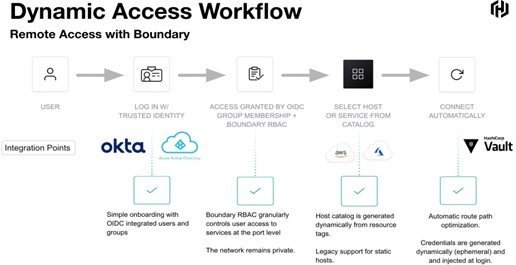
Image Source: Luke McCleary, HashiCorp
Using Boundary, the user never needs an SSH key or to know the public IP address, significantly strengthening overall security posture, and increasing flexibility, while reducing risks and costs. Since authentication and authorization are managed by Boundary using the user’s identity instead of a credential or an IP address, secure access can be tightly controlled based on roles and targets without exposure to the underlying network.
Adopting identity based solutions for both user access (Boundary) and secrets (sensitive information) management (Vault) together provide great value and solve many challenges for the IC, especially around identity driven workflows, dynamic secrets/credentials, automation, platform agnostic deployments, enhanced security, and reduced risk and costs. HashiCorp Vault is a key element of this approach and often the initial step to secure hybrid/multi-cloud environments (for additional information please see IC News article – A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community).
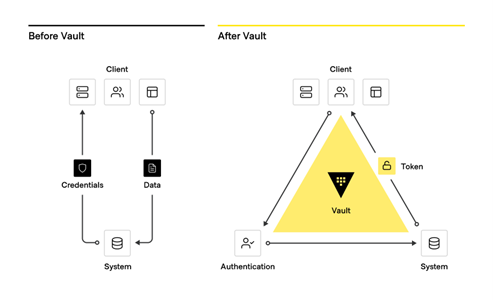
From traditional secrets workflow to modern secrets management with Vault
Vault Enterprise key capabilities:
- Manage secrets and protect sensitive data: Vault centrally stores, accesses, and deploys secrets across applications, systems, and platforms/infrastructure.
- Protect critical systems and customer data: Reduce the risk of breaches and data exposure with identity-based security automation and encrypting and securing application data (Encryption-as-a-Service) with one centralized workflow.
- Advanced auditing and reporting: Every operation with Vault is an API request/response and Vault audit logs contain every authenticated interaction.
Boundary sessions are time-bound and audited/logged. Boundary and Vault can stream audit logs into your existing workflow, saving time and money by removing the chance of human error. Here is an example of what this looks like using two layers of encryption to prevent a man-in-the-middle attack.
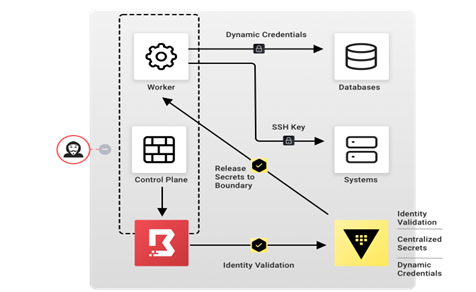
Image Source: HashiCorp
Boundary is self-managed and offers a secure connection to private endpoints without exposing your networks to public or managed service offerings.
How Does a Multi-Cloud Identity-Aware Proxy (IAP) Work?
The multi-cloud IAP sits between users and the infrastructure they connect to. An IAP has two general components:
- A Control Plane that manages the state around users under management, targets (systems), and access policies
- Worker Nodes are assigned by the control plane once a user authenticates and selects the target system. Conversely, these are stateless proxies requiring end-network access to the managed target systems
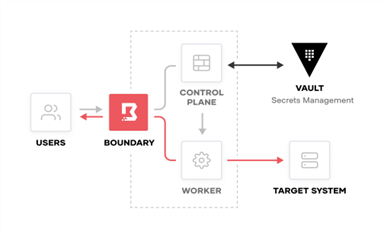
Image Source: HashiCorp
Users should be the center of any zero trust strategy since 82% of data breaches occur due to human error (GRC eLearning Blog). Traditional privileged access management (PAM) focuses on high-trust legacy approaches like trusting VPNs or SSH credentials. By adopting an identity-aware proxy, you can avoid untethered user access.
How does Boundary work?
Boundary provides secure access to hosts and critical systems without distributing and managing credentials, configuring firewalls, or exposing the organization’s private network. Traditionally, for users to access their resources, it’s required that organizations establish and maintain SSH bastion hosts and VPNs. The illustration below displays Boundary’s core workflow.
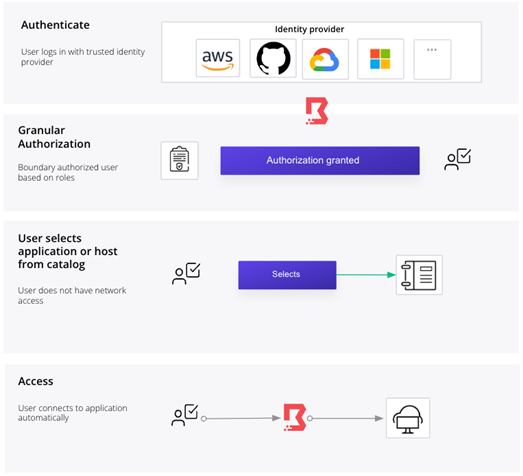
The core Boundary workflow consists of four stages:
- User Authentication: The user logs in with a trusted identity (based on the rules and policies) with a trust identity platform such as Azure Active Directory, Okta, Ping, or any other trust identity platforms supporting OpenID Connect.
- Granular Authorization: Boundary authenticates and authorizes users based on their roles and logical services, and tightly controls access and actions performed against systems.
- User-selected dynamic catalogs: The user selects their application or host from dynamic host catalogs.
- Access: Boundary streamlines connection to hosts by automating discovery and access configuration as workloads are deployed and changed.
Getting Started with a Multi-Cloud Identity-Aware Proxy (IAP)
The best place to start your zero trust and IAP adoption journey is with HashiCorpBoundary and HashiCorp Vault. Boundary is a new approach for identity-based user access, while HashiCorp Vault is an industry-wide, established, and widely adopted identity-broker and encrypted secrets management platform. Secret sprawl has been an increasing attack vector within the supply chain. Vault Enterprise can stop secret sprawl and achieve FIPS 140–2 compliance.
HashiCorp solutions are purposefully designed to operate independently or integrate and interoperate well with each other and other IT solutions. I recommend starting with HashiCorp Vault to stop secret sprawl and consolidate identity tools. Whether you are a fast follower or an early adopter, we know you want to stay caught up and we’re here to be your partner through the zero trust journey.
Conclusion – About HashiCorp
HashiCorp is secure platform automation for the hybrid/multi-cloud era. Adoption of secure platform agnostic, identity driven, solutions increase overall mission flexibility and effectiveness and helps future proof and position for advancing technologies. Many organizations implement this foundational approach to address some key use cases/workflows:
- Support Teleworking
- Protect Critical Resources
- Reduce Vulnerabilities and Threats
- Limit Exposure & Lateral Movement
- Improve Incident Response/Recovery
- Protect Sensitive Data
- Improve Visibility
Implementing an IAP (identity based, secure user connectivity by design) with centralized secrets management and establishing core zero trust workflows addresses the issue of secure user access and accelerates secure mission development and deployment.
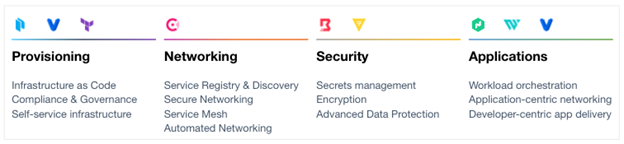
The HashiCorp suite of tools seeks to provide solutions for each layer of the cloud operating model and solves complex infrastructure challenges to meet mission needs. HashiCorp and our cloud infrastructure automation tooling are purposefully built to help complex organizations successfully deliver mission outcomes, securely, and at scale across any platform.
Additional Information:
White Paper: Unlocking the Cloud Operating Model
White Paper: Unlocking the Cloud Operating Model: Security
White Paper: A Leadership Guide to Multi-Cloud Success for the Intelligence Community
White Paper: Enabling Zero Trust Security in the Public Sector
Intelligence Community News Articles by HashiCorp:
- Enabling Zero Trust at the Device/Machine and Human/User Layers
- A Leadership Guide – Multi-Cloud Success for the Intelligence Community
- A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community
- A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community
- Just Start! – Implementing Zero Trust Workflows for the Intelligence Community
- How to Prevent Lateral Movement (Is the “Bad Actor” Already Inside?)
About HashiCorp
HashiCorp is the leader in multi-cloud infrastructure automation software. The HashiCorp software suite enables organizations to adopt consistent workflows to provision, secure, connect, and run any infrastructure for any application. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, and Nomad are downloaded tens of millions of times each year and are broadly adopted by the Global 2000. Enterprise versions of these products enhance the open source tools with features that promote collaboration, operations, governance, and multi-data center functionality. The company is headquartered in San Francisco and backed by Mayfield, GGV Capital, Redpoint Ventures, True Ventures, IVP, and Bessemer Venture Partners. For more information, visit www.hashicorp.com or follow HashiCorp on Twitter @HashiCorp.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.









