Enabling Zero Trust at the Device/Machine and Human/User Layers
Hybrid/Multi-cloud is the de facto standard operations model for modern IT organizations of all sizes, in all regions and in almost every industry. Driven by the need for increased mission effectiveness using digital transformation, Federal organizations are no different, and we see them investing significant resources in hybrid/multi-cloud deployments as the highest-of-priority initiatives.
Many organizations within the Department of Defense (DOD) and the Intelligence Community (IC) choose to innovate with HashiCorp Federal. HashiCorp’s products are cloud and platform-agnostic tools that offer organizations a methodology to seamlessly optimize their existing workflows and facilitate their hybrid/multi-cloud strategy by making it easier to deploy applications across most any platform at scale.
This discussion will expand on topics from the article: Getting Started with Zero Trust Security. The adoption of Zero Trust can be challenging as Zero Trust principles and approaches are usually unique for every environment and organizations are faced with the dilemma of how to start adopting zero trust. This article will expand on those foundational principles and discuss the challenges at the device/machine and human/user layers/pillars.
Shift to dynamic infrastructure necessitates the need for Zero Trust
Traditionally, devices/machines are connected and secured by a fleet of network infrastructure, such as routers, switches, load balancers and firewalls and humans/users leveraging complex tooling and approaches to gain access. Organizations focus on managing and securing device/machine and user traffic flowing in and out of the data center. The network is protected and secured by IP centric coarse-grained network segments and infrastructure devices. An IP centric approach as a security control point is challenged by the shifting demands of a dynamic/ephemeral environment as managing access across multiple dynamic platforms and associated IP’s at scale becomes brittle and complex.
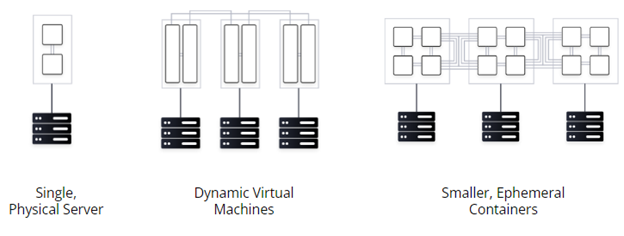
Static infrastructure was historically straightforward to secure and was typically within the well defined 4 walls of a datacenter. As mission needs change and technology advances hybrid/multi cloud adoption ensures these environments become less static, harder to control, and offer less visibility. Securing ephemeral and dynamic infrastructure is increasingly challenging because it has no defined perimeter, multiple entry/exit points, and scales with demand. With this shift, we are faced with the challenge of moving from an increasingly ineffective and complex perimeter based, IP centric, model of security to embracing a zero trust security model.
With zero trust security we trust nothing, and authenticate and authorize everything. Critical to enabling a zero trust approach is establishing identity based security. This identity driven workflow requires a fundamental shift from traditional IP as a security control point. Enabling devices/machines and humans to authenticate and authorize based on identity is a core element of a zero trust based hybrid/multi-cloud-first organization. This key zero trust approach can be implemented through the use of a platform agnostic solution that creates a consistent environment that enables device/machine and human identity-based authentication and authorization, decoupled from IP centric approaches.
Zero Trust Security: Trust Nothing. Authenticate and Authorize Everything
Zero trust security is predicated on securing everything based on trusted identities. These are the four foundational categories (pillars, if using the DISA Zero Trust Reference Architecture) for identity-driven controls and zero trust security:
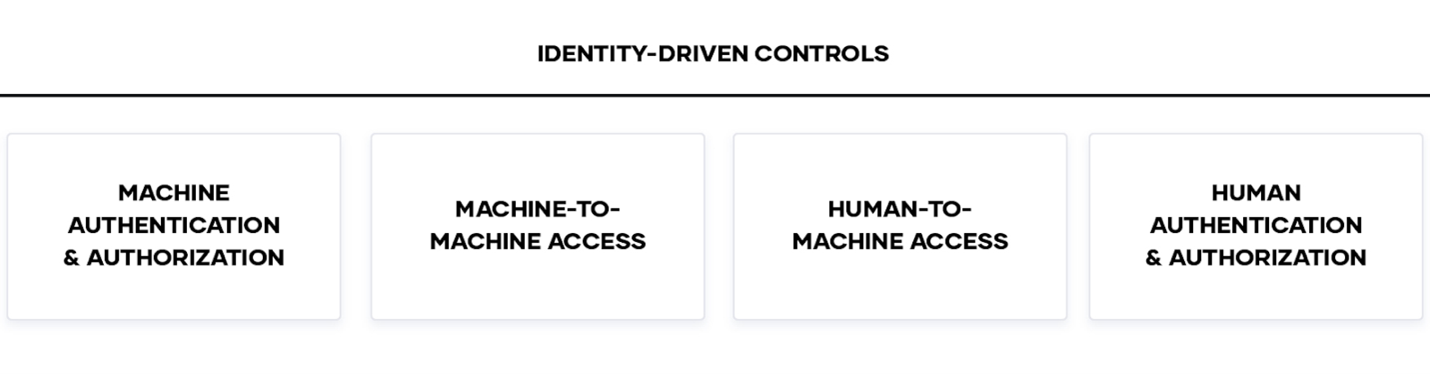
Enterprises are embracing zero trust security emphasizing these fundamental use cases:
- Machine Authentication & Authorization: Enterprises need to centrally store, access, and distribute dynamic secrets like tokens, passwords, certificates, and encryption keys across any public or private cloud environment.
- Machine-to-machine Access: Enterprises need to enable machine-to-machine access by enforcing authentication between applications and ensuring only the right machines are talking to each other.
- Human Access and Authorization: Enterprises need to secure access to applications and critical systems with fine-grained authorizations without managing credentials or exposing a network.
The migration to hybrid/multi cloud means organizations are rethinking how to secure their environment. Traditional solutions are no longer sufficient with the adoption of hybrid/multi cloud as IP-based perimeters and access are replaced by ephemeral IP addresses and a constantly changing workload with the need to access shared resources. Managing access and IPs at scale becomes brittle and complex. This is driving the need for a zero trust approach to security in the cloud based on dynamic, identity-driven controls. This is the basis of device/machine and human-to-machine zero trust security.
HashiCorp’s solutions enable organizations to adopt the Cloud Operating Model, which in turn enables enterprises in establishing zero trust security for hybrid/multi-cloud environments. At HashiCorp, our security model is predicated on the principle of zero trust and identity-based access and security. In order for any machine or human to do anything, they must authenticate who or what they are, and their identity and policies define what they’re allowed to do. Here’s how the HashiCorp offerings can help adopt the core pillars and make zero trust security work:
- Machine authentication and authorization – HashiCorp Vault (Discussed in this article)
- Machine-to-machine access – HashiCorp Consul (Discussed in previous article – “Enabling Zero Trust at the Application Layer” published here )
- Human-to-machine access – HashiCorp Boundary (Discussed in this article)
Enabling Zero Trust at the Device/Machine (Vault)
Device/Machine Authentication and Authorization
HashiCorp Vault enables enterprises to centrally store, access, and distribute dynamic secrets like tokens, passwords, certificates, and encryption keys across any hybrid, public or private cloud environment. Unlike burdensome ITIL-based systems, HashiCorp Vault solutions issue credentials to people, applications, and devices/machines in a dynamic, identity based, fashion, creating a secure, efficient, and truly hybrid/multi-cloud solution. Vault helps organizations reduce the risk of breaches and data exposure with identity-based security automation and encryption-as-a-service. Any user, device/machine, application transacting with Vault is considered a Client.
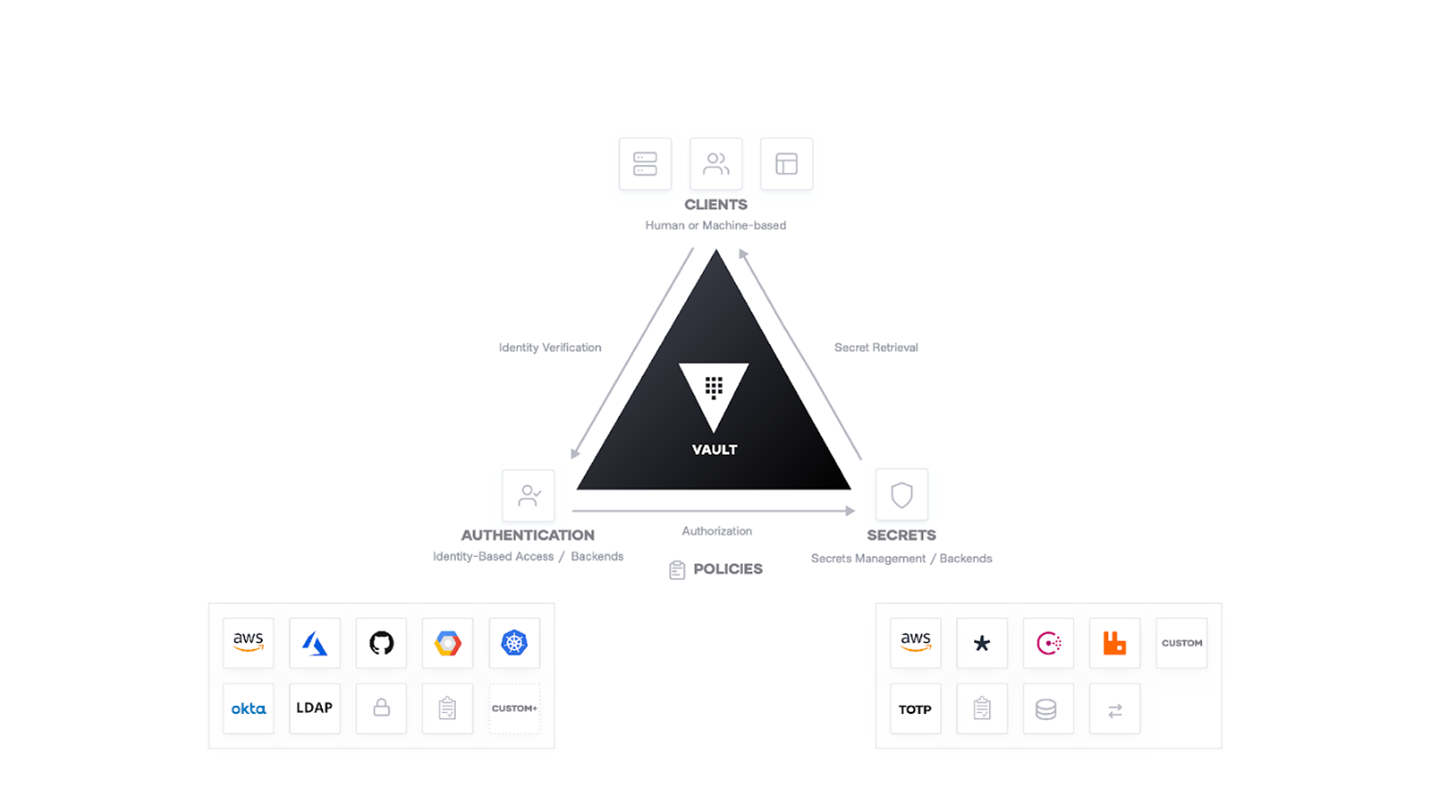
Vault is an identity-based secrets and encryption management system with zero trust built in by design. In Vault, a secret is anything that you want to tightly control access to by authenticating against existing trusted sources of identity such as Active Directory, LDAP, Kubernetes, and cloud platforms. Vault supports hybrid, public clouds, and private data centers, and a broad range of endpoint systems. Request secrets for any system through one consistent, audited, identity based, secured workflow. Examples work best to showcase Vault – see the use cases.
The key features of Vault are:
- Secure Secret Storage: Arbitrary key/value secrets can be stored in Vault. Vault encrypts these secrets prior to writing them to persistent storage, so gaining access to the raw storage isn’t enough to access your secrets.
- Identity Brokering: Authenticate and access different clouds, systems, and endpoints using trusted identities. Leverage multiple identities across different platforms with single policy enforcement. Integrate trusted identities in the same application workflow to reduce operational overhead.
- Dynamic Secrets: Vault can generate secrets on-demand for some systems, such as AWS or SQL databases. For example, when an application needs to access an S3 bucket, it asks Vault for credentials, and Vault will generate (and revoke automatically at expiration) an AWS keypair with valid permissions on demand.
- Data Encryption: Vault can encrypt and decrypt data without storing it. This allows security teams to define encryption parameters and developers to transmit and store encrypted data without having to design their own encryption methods.
- Leasing and Renewal: All secrets in Vault have a lease associated with them. At the end of the lease, if not renewed, Vault will automatically revoke that secret.
- Revocation: Vault has built-in support for secret revocation. Vault can revoke not only single secrets, but a tree of secrets. Revocation assists in key rolling as well as locking down systems in the case of an intrusion
Securing access with static IPs and ephemeral infrastructure at scale is complex and brittle. The hybrid/multi cloud requires a fundamentally different approach starting with understanding the network as inherently “low trust” and then adopting the securing of infrastructure, devices/machines, and application services, based on trusted identities and zero trust principles.
The idea of Identity is to maintain the clients who are recognized by Vault as separate authenticated entities. As such, Vault provides an identity management solution for users, devices/machines, and applications, through the Identify Secrets Engine. Vault is identity based and zero trust by design.
Authentication in Vault is the process by which user or machine supplied information is verified against an internal or external system. Auth Methods are the components in Vault that perform authentication and are responsible for assigning identity and a set of policies to a client. In all cases, Vault will enforce authentication as part of the request processing. Before a client can interact with Vault, it must authenticate against an auth method (Vault supports multiple auth methods including LDAP, AppRole, and more). Upon authentication, a token is generated which may have an attached policy, which is mapped at authentication time. This authentication process is a key enabler for identity based zero trust workflows for devices/machines.
With Vault, organizations can authenticate, and access different clouds, systems, and endpoints using trusted identities and enable secure access to secrets, systems, and data. Identity is scale independent, unlike IP centric approaches which require complex infrastructure, ever changing rules, and frequent updates.
Identity Brokering is a core component and guiding principle of Vault.
- Authenticate and access different clouds, systems, and endpoints using trusted identities
- Leverage multiple identities across different platforms with single policy enforcement
- Integrate trusted identities in the same application workflow to reduce operational overhead
With Vault’s identity brokering and identity-based workflows it becomes a key component in a zero trust architecture. Organizations can improve security and apply key Zero Trust principles (such as identity driven, authentication/authorization, time bound, auditing, data protection) to enable identity-based workflows for devices/machines.
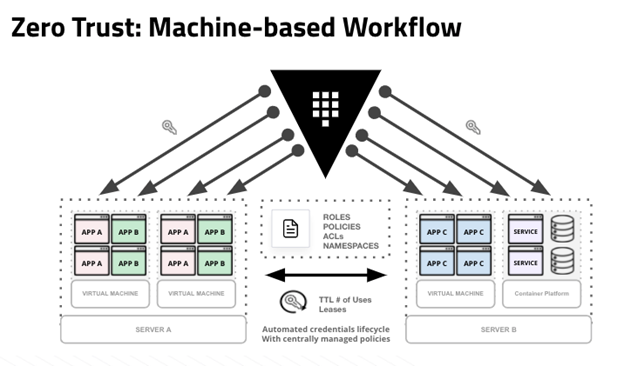
Adoption of Vault and enabling Zero Trust at the device/machine layer typically follows a three-stage approach for most organizations. First, organizations can establish a foundation of secrets management services with Vault and then standardize on delivering an identity-based approach across various operational platforms. Second, use Vault’s Identity Brokering capabilities to establish trusted identities for all clients, including devices/machines. Third, migrate from IP centric patterns and innovate/adopt zero trust based workflows at the device/machine layer to authenticate and authorize using trusted identities with Vault.
For most IC and DoD enterprises, the goals of digital transformation efforts mean delivering new mission and customer value more quickly, securely, and at a very large scale. The hybrid/multi cloud is an inevitable part of this initiative as it presents the opportunity to rapidly deploy on-demand services with limitless scale and can leverage Vault to enable Zero Trust at the Device/Machine Layer.
Enabling Zero Trust at the Human/User Layer
HashiCorp Boundary: Simple and secure remote access
Traditional solutions for safeguarding human/user access required the distribution and management of SSH keys, VPN credentials, and bastion hosts, which creates increased complexity, risks around credential sprawl and exposure, and users having access to entire networks and systems.
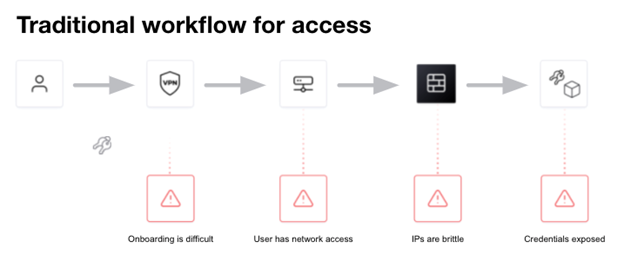
HashiCorp Boundary secures access to applications and critical systems with fine-grained authorizations without managing credentials or exposing your network. Boundary enables access to any system from anywhere based on user identity. Boundary enables simple and secure access to dynamic infrastructure by:
- Identity-based access controls: Streamline just-in-time access to privileged sessions for users and applications. Tightly control access permissions with extensible role-based access controls.
- Access Automation: Define your perimeter of resources, identities, and access controls as code through Boundary’s fully instrumented Terraform Provider. Automate the discovery of new resources and enforcement of existing policies as resources are provisioned.
- Session Visibility: Security administrators gain ability to monitor and manage the privileged sessions established with Boundary. Export session logs to an analytics tool.
In the shift to the cloud, organizations need secure access to targets both internal and beyond their own perimeter. The use of different identity platforms for federated systems of record is a common approach. Leveraging these trusted identity providers is the principle of identity-based access and security. HashiCorp products have deep integration with leading identity providers.
Boundary enables an identity based workflow at the human-to-machine access layer and provides a secure way to access hosts and critical systems without having to manage credentials or expose your network, and is entirely open source.
- Boundary authenticates with any trusted identity provider and authorizes access based on granular, logical roles and services.
- Boundary manages dynamic infrastructure and integrates service registries so hosts and service catalogs are kept up-to-date.
- Boundary reduces risk of leaking credentials with dynamic secrets and just-in-time credentials. Automate credential brokering to securely access services and hosts with HashiCorp Vault.
- On-demand identity-based access to infrastructure. Securely connect trusted identities to logical services without having to create or store credentials or access.
- Scale access management in dynamic environments. Scale access management by defining access controls around logical services instead of IP-based access policies.
- Streamline remote access with easy-to-use CLI, API or UI. Make it easy to access all applications and systems through a single workflow that works with existing tooling.
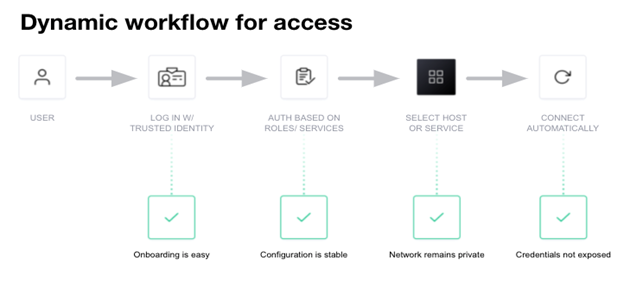
Boundary is a secure remote access solution that provides an easy way to allow access to applications and critical systems with fine-grained authorizations based on trusted identities and to protect and safeguard access without exposing the underlying network.
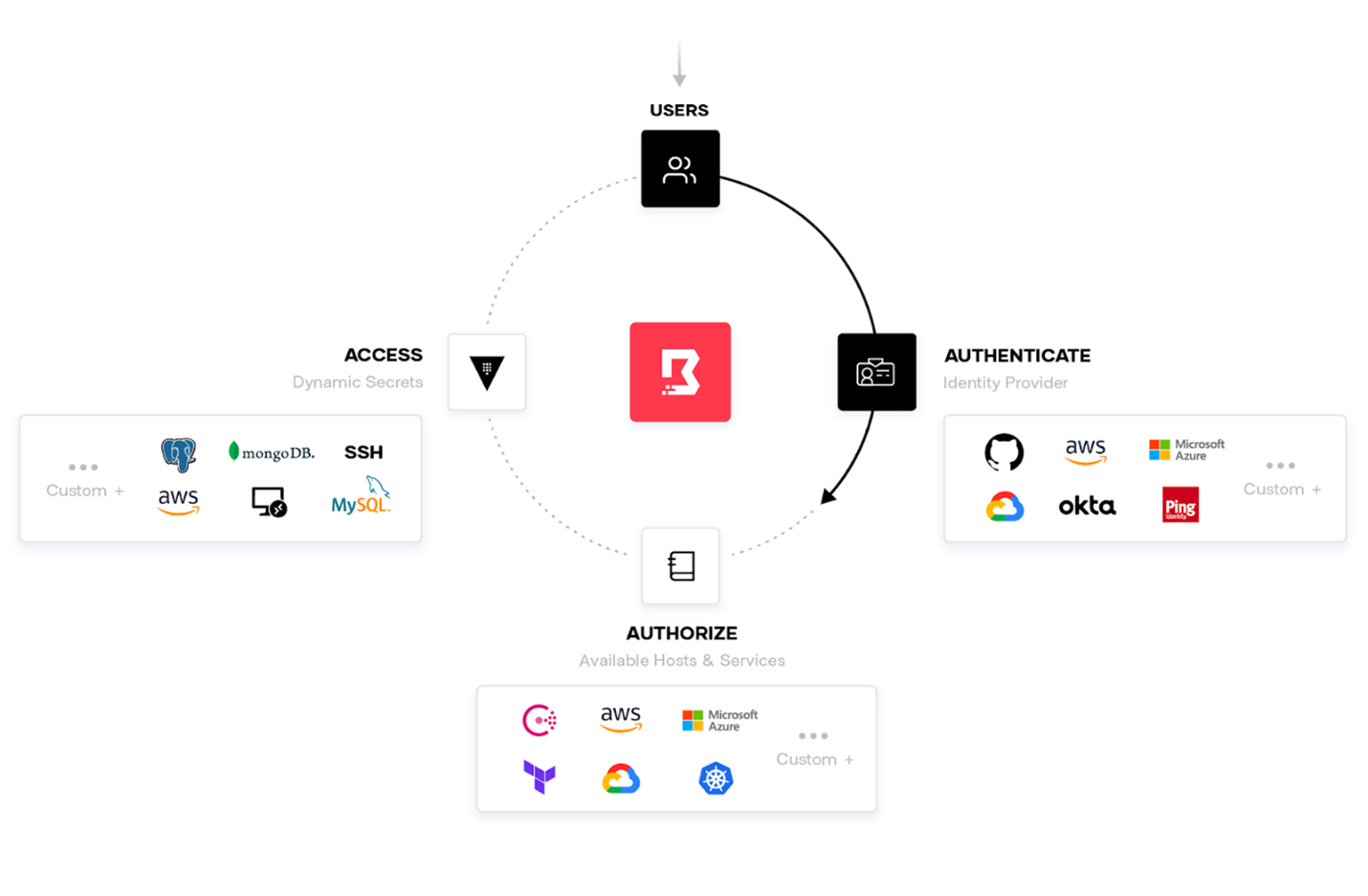
Boundary provides:
- Platform-agnostic proxy for dynamic targets
- No SSH keys or VPN credentials to manage
- Just-in-time credentials via HashiCorp Vault
- Brokering Vault secrets and dynamic secrets management
Boundary reduces or eliminates the need for traditional approaches like SSH bastion hosts or VPNs that require distributing and managing credentials and configuring network controls like firewalls, increasing risk and exposing the private network. Boundary provides a secure way to access hosts and critical systems without having to manage credentials or expose the network and enables the human/user identity based zero trust workflow.
Summary
At HashiCorp, our security model is predicated on the principle of identity-based access and security, foundational for Zero Trust solutions. For any machine or user to do anything, they must authenticate who or what they are, and their identity and policies define what they’re allowed to do. HashiCorp offerings can help with key zero trust layers/pillars:
- Machine Authentication & Authorization: HashiCorp Vault solutions issue identity based credentials to both people and machines in a dynamic fashion, creating a secure, efficient, hybrid/multi-cloud solution.
- Machine-to-Machine access: HashiCorp Consul enables machine-to-machine access by enforcing authentication between applications and ensuring only the right machines are talking to each other.
- Human-to-Machine access: HashiCorp Boundary secures access to applications and critical systems with fine-grained authorizations without managing credentials or exposing your network.
HashiCorp’s technology adoption journey is a straightforward path that IC and DoD organizations can follow enabling a more simplified and scalable identity based approach to agnostic hybrid/multi-cloud while enabling Zero Trust at the Device/Machine (Vault) and Human/User (Boundary) Layers.
HashiCorp’s framework for Zero Trust: Trust Nothing, Authenticate and Authorize Everything.
About HashiCorp
HashiCorp provides infrastructure automation software for multi-cloud environments, enabling enterprises to unlock a common cloud operating model to provision, secure, connect, and run any application on any infrastructure. HashiCorp tools allow organizations to deliver applications faster by helping enterprises transition from manual processes and ITIL practices to self-service automation and DevOps practices. For more information, visit hashicorp.com.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.







