A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community

From IC Insider HashiCorp
By Jarrod Gazarek and Tim Olson
Increasing threats and escalating cyber-attacks make securing hybrid/multi-cloud (cloud) operational environments critical for the Intelligence Community (IC). Security in a single cloud (C2S) is difficult and now with the era of hybrid cloud environments (Commercial Cloud Enterprise (C2E)) it’s not only essential it’s increasingly complex and challenging. This article will focus on approaches to establish secure foundations and practices for the effective adoption of hybrid cloud. For additional information on the practical adoption of hybrid cloud platform approaches please refer to A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community (IC News, July 6, 2022).
Effective digital transformation practices mean adopting industrialized workflows that can securely deliver new business and mission objectives quickly, on demand, and at a very large scale. Governance/Security, is one of the four key challenges (Skills gap, Scalability, Governance, and Untenable Costs) discussed in A Leadership Guide – Multi-Cloud Success for the Intelligence Community (IC News, April 18, 2022).
Our previous article discussed how establishing a platform approach is instrumental in achieving the maximum benefits from a hybrid cloud. Effective platform teams deliver shared infrastructure, runtimes, services, standardized workflows, enabling secure operational cloud adoption. Organizations often position their hybrid cloud platform as a product, a key principle of user-centered design.
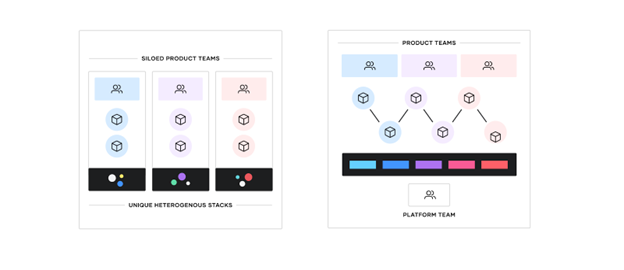
While most enterprises have established enterprise data centers and at least one cloud provider we are seeing the shift to hybrid/multi-cloud environments (C2E). We are also seeing these enterprises offering a wider range of services and resources. As a result, the challenge for most enterprises is how to consistently deliver mission applications rapidly and securely. Compounding this challenge, the underlying IT primitives have expanded encompassing disparate, complex, operational models.
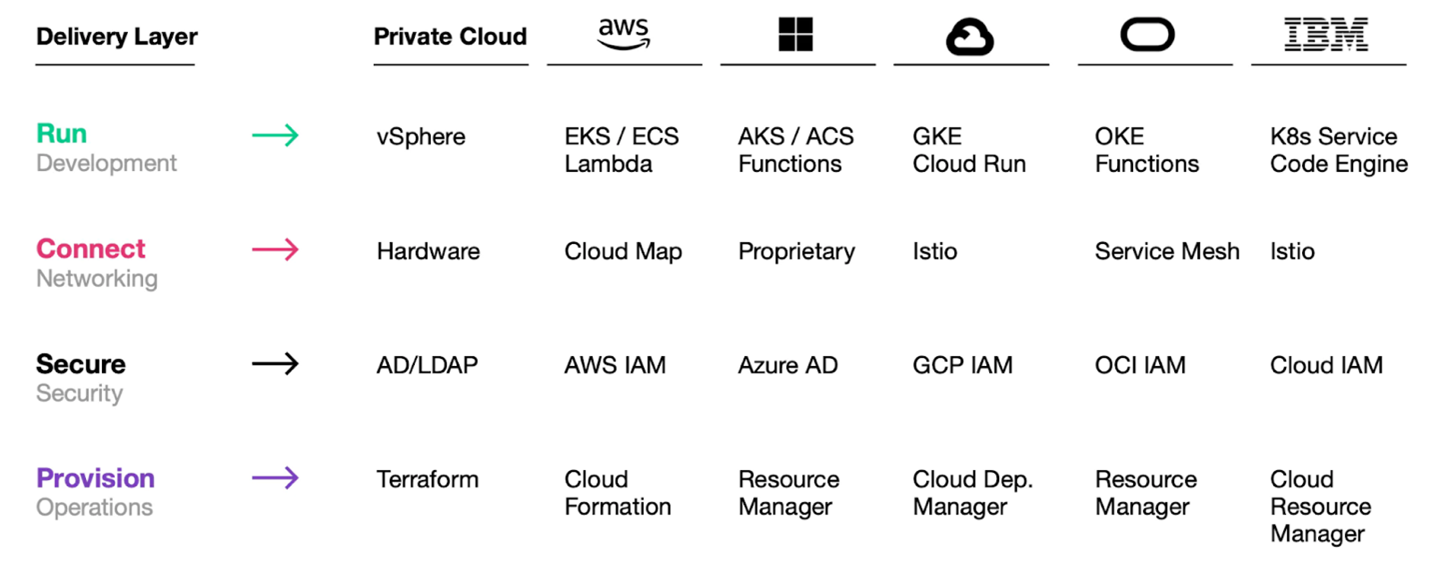
This shift is highly disruptive to traditional security models. For hybrid cloud computing to be effective and adaptable for mission deployments there needs to be consistent secure approaches and workflows that are reused at scale across multiple environments and cloud providers. Fundamentally, this requires:
- Compliant Platforms / Infrastructure with consistent secure workflows
- Secure platform secrets (sensitive data/information) management
- Dynamic Secrets and Encryption everywhere
- Secure service/application level connectivity
- Identity based security and Identity driven access
- Zero Trust frameworks and workflows
Achieving Hybrid/Multi-Cloud Success: Security Considerations
Adoption of these practices establishes shared service layers across the hybrid/multi-cloud and presents an industrialized process for secure application delivery, all while taking advantage of the dynamic nature of each layer of the cloud. The platform team’s responsibility is to keep the platform stable, resilient, performant, and secure.
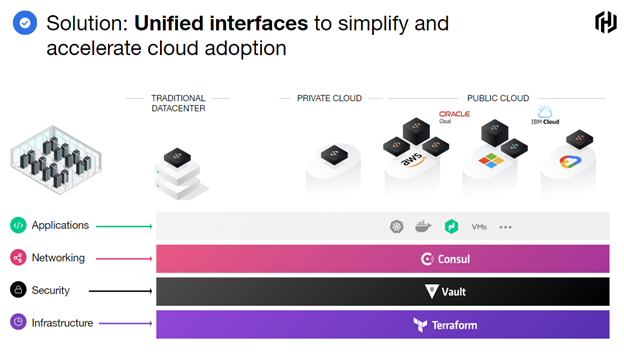
Adopting Auditing and Compliance
Establishing automation with built in policy enforcement (compliance) will accelerate auditing procedures, improve and enforce compliance, and increase mission readiness. This will deliver predictable, repeatable, hardened deployments increasing platform level security and mission capabilities. HashiCorp solutions help organizations build, maintain, and audit compliant infrastructure platforms across all layers of the cloud.
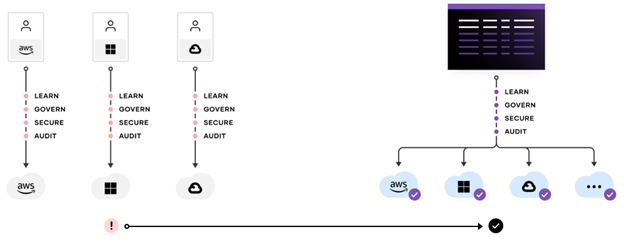
Provision and maintain compliant infrastructure
HashiCorp Terraform Enterprise is an infrastructure as code (IaC) solution and provides a consistent, automated, workflow to manage hundreds of hybrid cloud resources and services. Terraform Enterprise allows organizations to ensure infrastructure platforms are built and managed in a compliant manner at scale.
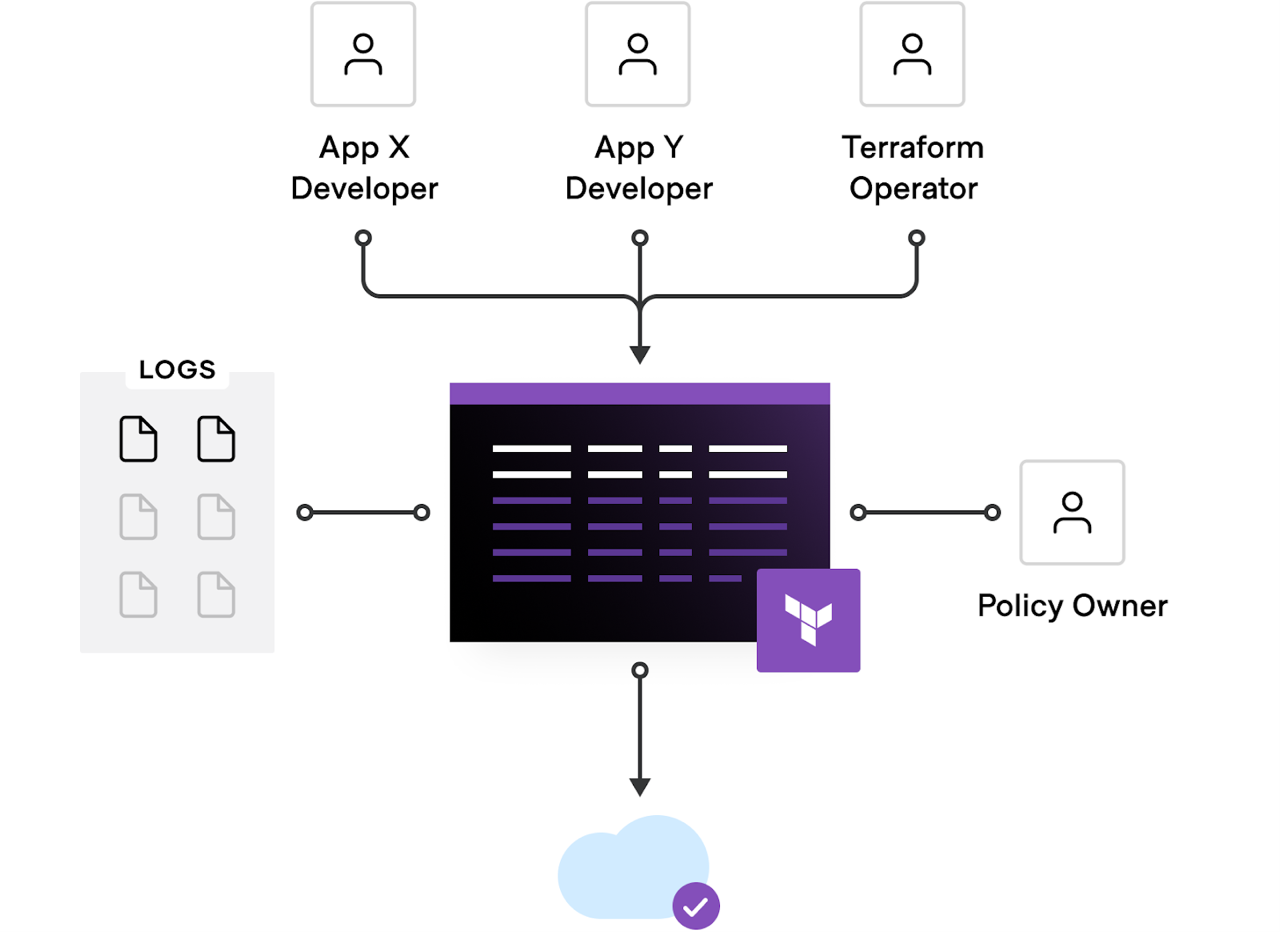
Automated policy enforcement and audit logs provide a system of record to track all provisioned infrastructure
Key features Terraform Enterprise provides to enable compliant infrastructure include:
- Infrastructure as code (IaC): Automate everything through code and maintain compliance more with hardened modules ensuring provisioning of secured and standardized infrastructure.
- Policy as code (PaC): HashiCorp Sentinel creates and enforces policy as code, embedded in the workflow.
- Version control system (VCS) integration: Connections to major VCS providers allowing for automated management and running of configuration (IaC) and policy (PaC) files.
- Infrastructure state: State files provide a holistic view of current and previously configured versions of your infrastructure enabling compliance checks and auditing.
Build consistent, compliant machine images for every environment
HashiCorp Packer allows for creation of identical, hardened, machine images that are verified as compliant (Golden images) across multiple platforms from a single source configuration. These golden images enable rapid mission deployment across multiple platforms.
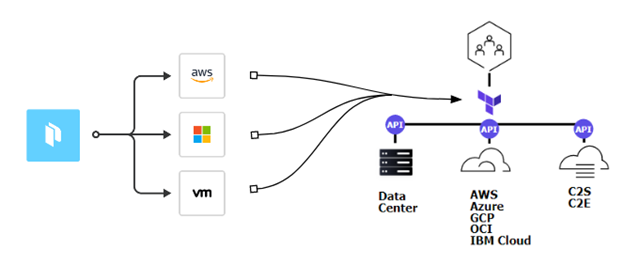
Compliant Automated Workflows – Adopting Policy as Code (PaC)
Policy as code is the next phase of compliant automation (Infrastructure as Code (IaC) was the first phase). PaC limits exposure by codifying and enforcing policies to ensure infrastructure deployments are compliant. Together IaC and PaC empower organizations to rapidly and securely deploy any infrastructure platform for any application.
Using a PaC framework (HashiCorp’s Sentinel) provides embedded compliance and governance without requiring a shift in the overall team workflow. Codified policies enforce security and operational best practices across all hybrid cloud provisioning. PaC allows platform teams to establish “guard rails” for compliant environments accelerating mission delivery by abstracting the definition of the policy from the execution of the policy.
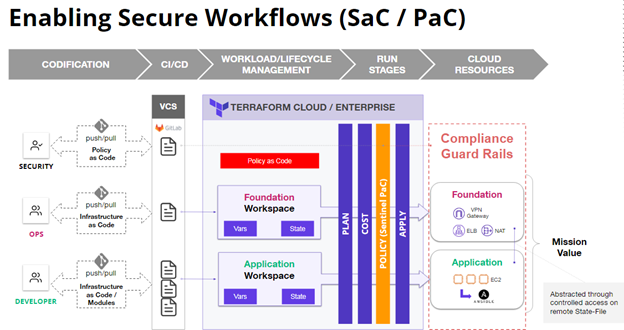
Sentinel – Policy as Code framework for HashiCorp Enterprise Products
HashiCorp Sentinel is a policy as code (PaC) framework to enable logic-based policy decisions that can be extended to source external information to make decisions. Sentinel provides these key advantages when deploying secure platforms:
- Embedded: Enable policy enforcement in the data path to actively reject violating behavior instead of passively detecting.
- Multiple enforcement levels: Allow policy writers to warn or reject offending behavior.
- External information: Source external information to make holistic policy decisions.
- Hybrid/Multi-cloud compatible: Ensure infrastructure changes are within mission and regulatory policy across every infrastructure provider.
Manage secrets and implement advanced data protection and encryption everywhere
Dynamic hybrid cloud infrastructure means a shift from traditional host-based and network centric (high trust), to networks across multiple clouds and no clear network perimeter (low/zero trust). This requires that platforms and applications are explicitly authenticated and authorized to perform sensitive operations, while being tightly audited.
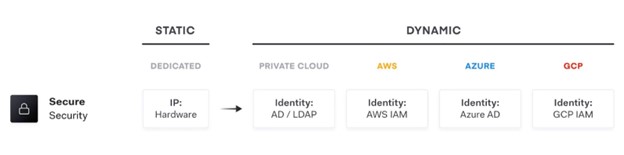
Static to Dynamic infrastructure at the secrets management layer
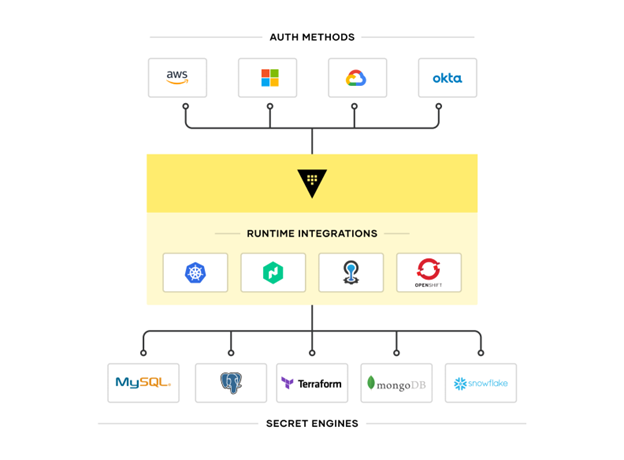
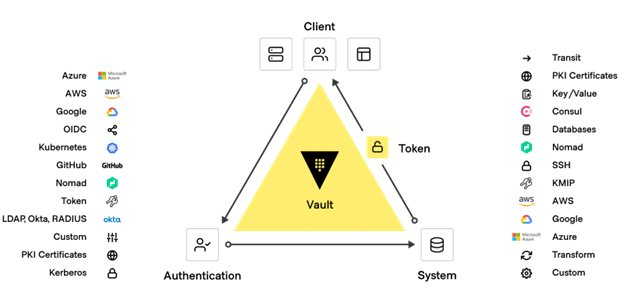
HashiCorp Vault Enterprise enables organizations to manage secrets, protect sensitive data, and control access to conform to relevant compliance frameworks across operational platforms. Vault Enterprise is identity based. Vault authenticates these identities and uses them as a system of record to manage and enforce access to secrets and systems.
Vault Enterprise key capabilities:
- Manage secrets and protect sensitive data: Vault centrally stores, accesses, and deploys secrets across applications, systems, and platforms/infrastructure.
- Protect critical systems and customer data: Reduce the risk of breaches and data exposure with identity-based security automation and encrypting and securing application data (Encryption-as-a-Service) with one centralized workflow.
- Advanced auditing and reporting: Every operation with Vault is an API request/response and Vault audit logs contain every authenticated interaction.
Enabling Identity-based Security
Managing access to secrets in a multi-cloud world consists of two primary user types: humans and machines. Managing secrets for humans is well established. Machines are a different issue as they can include servers, virtual machines, containers, applications, microservices, and more, all potentially needing access to different systems and secrets. When it comes to managing secrets with machines in a hybrid/multi-cloud environment, the dynamic, identity based, nature of HashiCorp Vault comes to the forefront.
Vault’s identity system is an essential capability that enables brokering identities between different platforms into unified identities to allow applications to work across platform boundaries. Whether a machine or user is looking to create and distribute organizational secrets, Vault solves managing this access based on trusted identities.
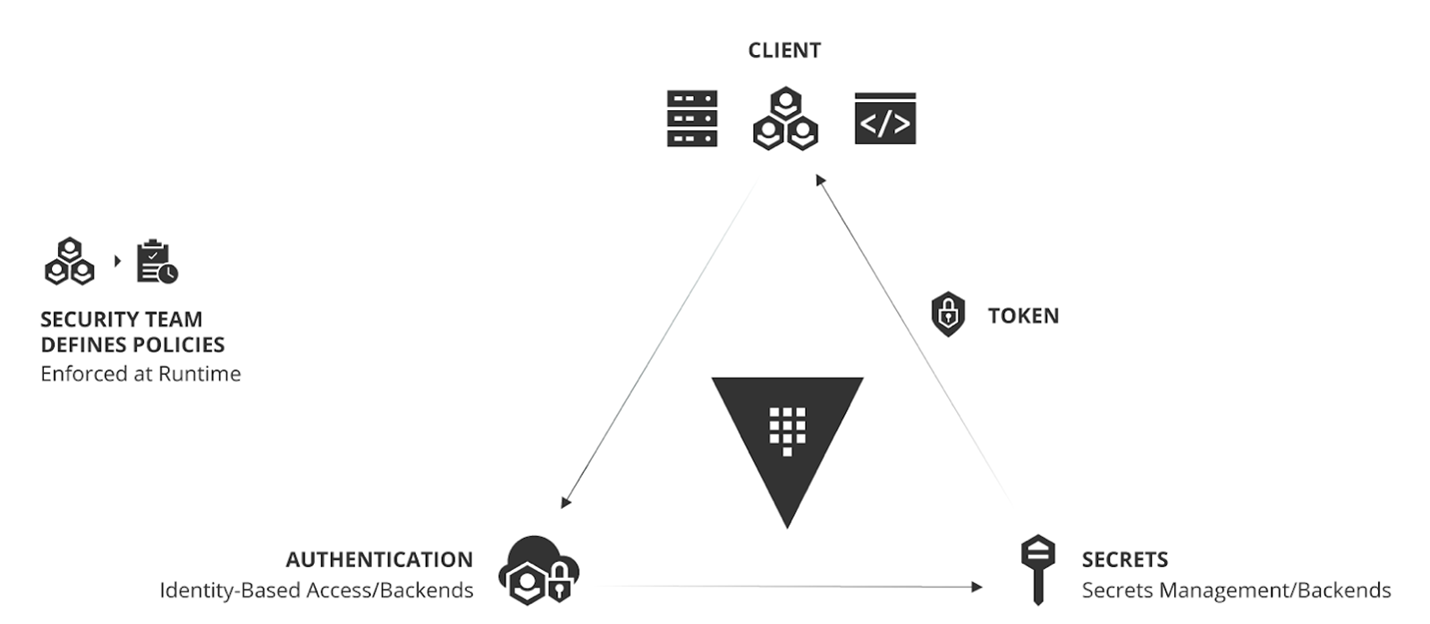
Operating Model for Identity-based Security and Secrets Management
Vault enables IC organizations to provide secrets management and data encryption services across platforms, applications, and mission teams.
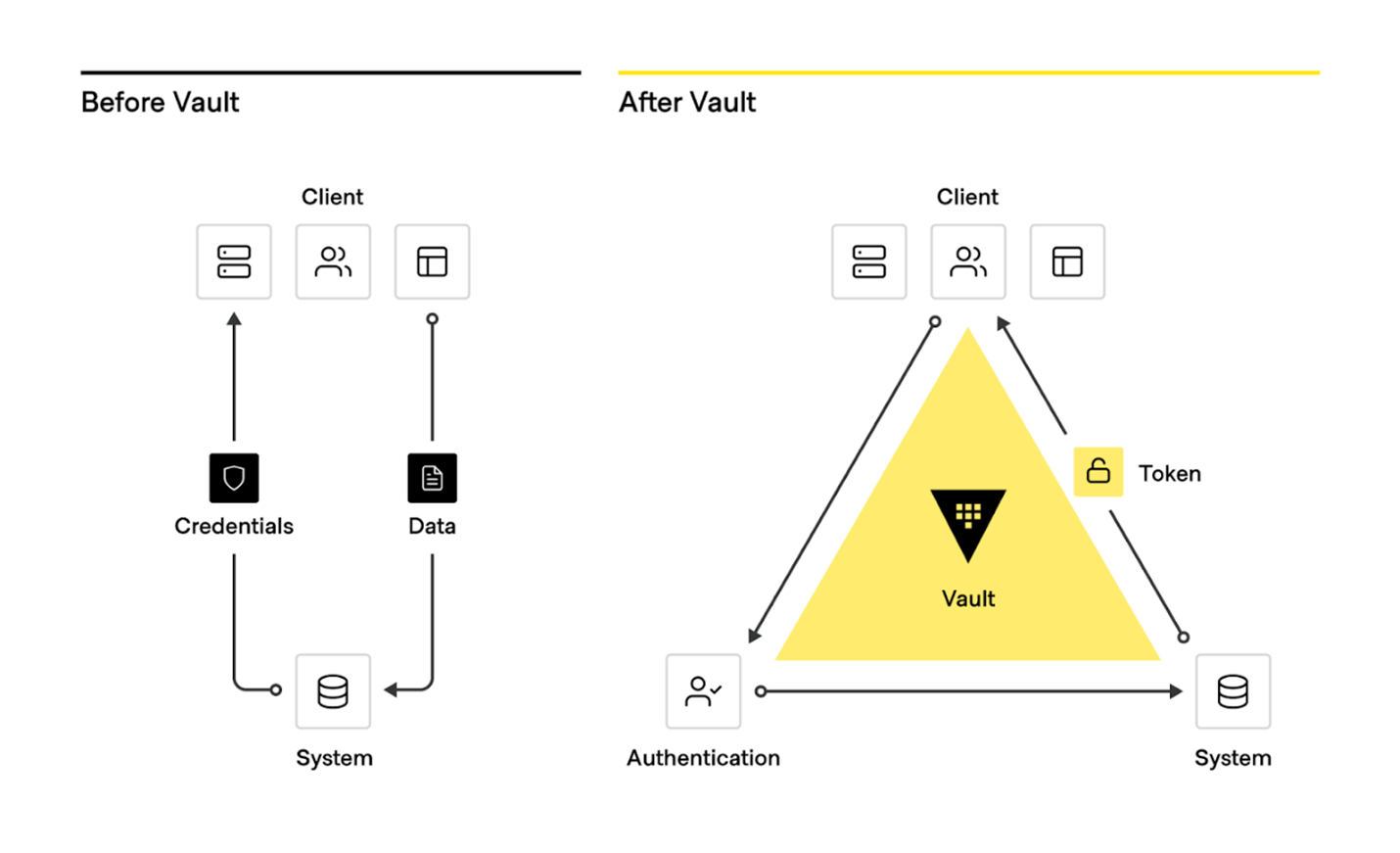
From traditional secrets workflow to modern secrets management with Vault
Dynamic Secrets and Encryption as a Service
Overall security posture can be significantly increased using dynamic secrets in Vault. This will enable secrets to be created on demand and time bound. Vault, as a central secrets manager, can revoke all secrets in the event of a breach or attack.
Vault can provide a central, standardized, encryption as a service (EaaS) as a consistent API for key management and cryptography. The Vault API exposes cryptographic operations to secure sensitive data without exposing encryption keys. Vault also can act as a certificate authority (root or intermediary) to provide dynamic short-lived certificates to secure communications with SSL/TLS.
The adoption of this operating model for identity-based security and secrets management with Vault is an inevitable shift for enterprises aiming to rationalize security in a world of multiple clouds.
Secure service level connectivity (Application Level Networking)
HashiCorp Consul Enterprise is a secure service networking solution built for dynamic, hybrid cloud environments, and is optimized to ensure secure networking best practices. Consul helps organizations discover and securely connect services running in any environment.
- Discover services: Consul is a dynamic service registry that can be leveraged as a single source of truth for any service running across all environments.
- Secure service networking: Discover and securely connect services based on identity and intentions. Enables a “defense in depth” approach to implement a zero trust environment.
- Automated networking (Network Infrastructure Automation): Automate network processes using Consul-Terraform-Sync. Trigger automated network infrastructure updates using Terraform that can then be validated against Sentinel policies.
- Securely access services: Federated service mesh provides the means to manage and ensure secure, identity based, connectivity between services in an east-west pattern.
HashiCorp Consul enables platform teams to manage hybrid/multi-cloud networks by discovering and securely connecting services across most any operational platform.
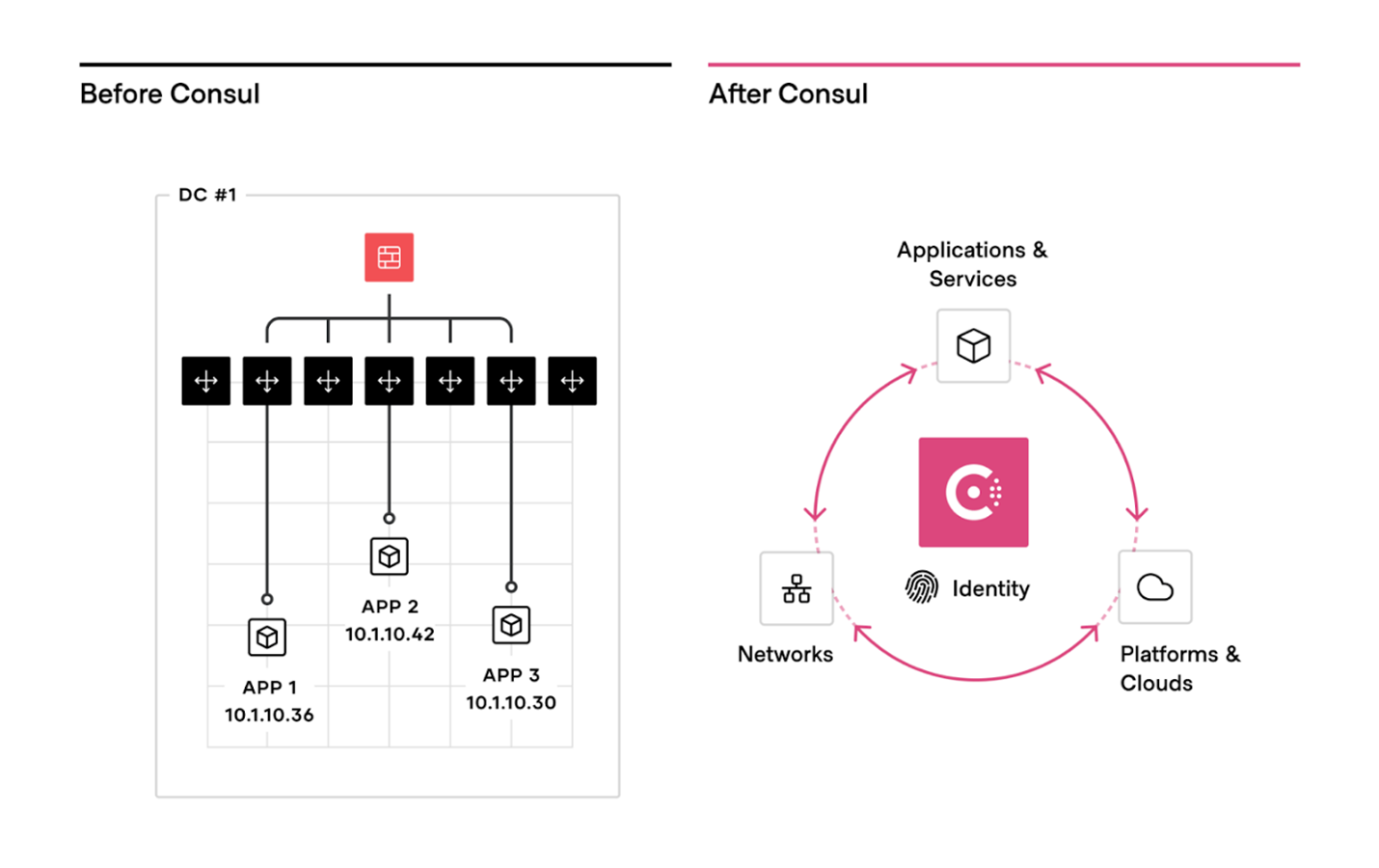
Network Infrastructure Automation
An essential element of reducing the operational complexity and strengthening the security posture of existing networking infrastructure is through network automation. Instead of a manual, ticket-based process to reconfigure load balancers and apply firewall rules every time there is a change in service network locations or configurations, Consul can automate these network operations using Terraform. This enables highly dynamic infrastructure that can scale beyond static-based approaches and automatically update firewalls, load balancers, etc., to ensure network configuration and security is current within the operational environment.
Zero Trust Networking with Service Mesh and API Gateway
Consul provides a platform agnostic distributed service mesh that pushes routing, authorization, and other networking functions to the endpoints in the network. This makes the network topology simpler and easier to manage, reduces the need for expensive middleware devices within east-west traffic paths, and makes service-to-service communication more secure, reliable and scalable.
Adding Consul’s API Gateway provides consistent control and security for how north-south traffic is handled. This security posture is achieved with automatic mutual TLS encryption and identity-based authorization.
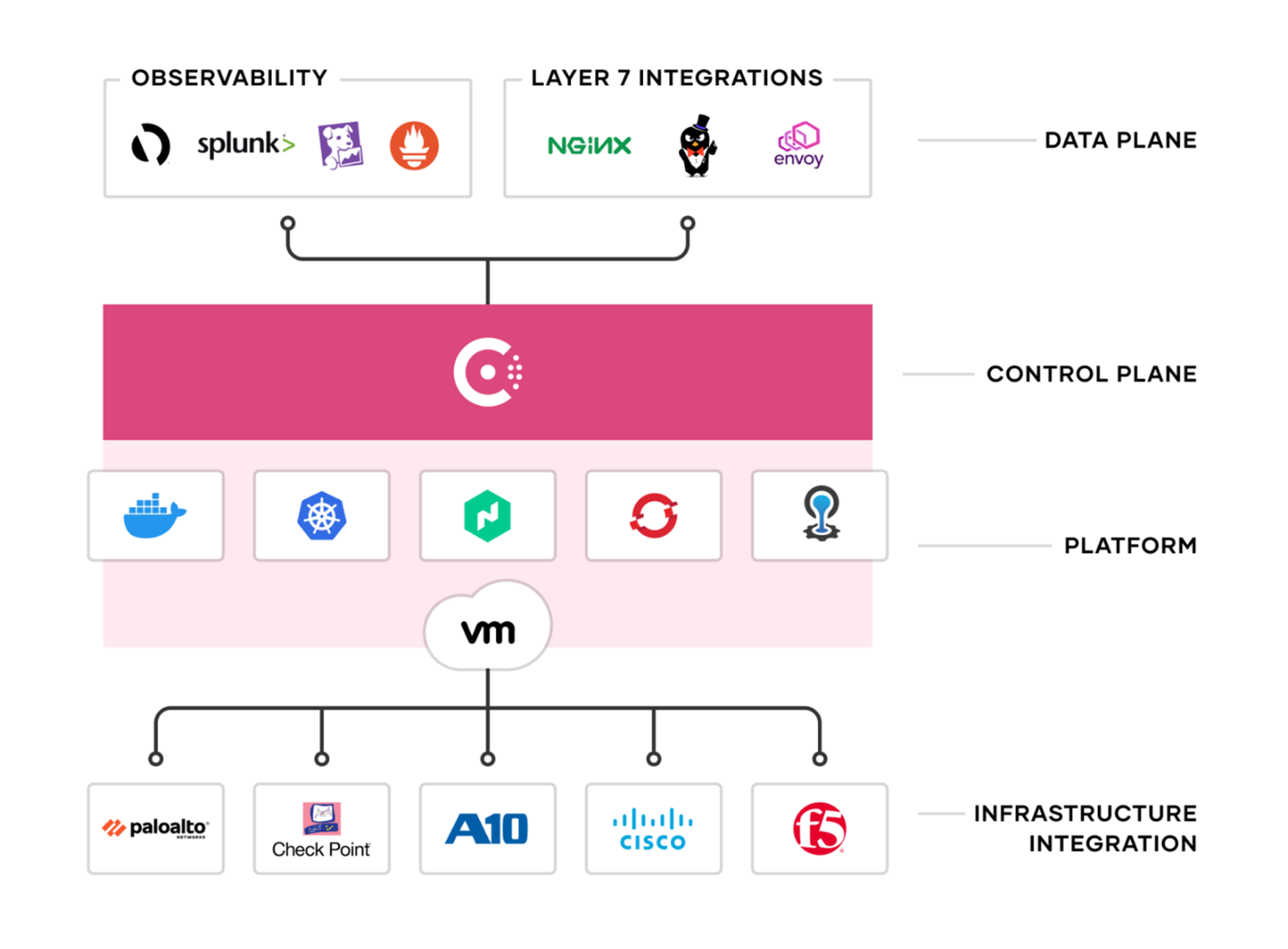
HashiCorp Consul provides a single control plane to enable secure service networking.
For increased security, Consul can be integrated with Vault for centralized PKI and certificate management with automatic certificate rotation on both the control plane and data plane. Consul Federated Service Mesh secures service connections across any hybrid cloud environment and on any runtime.
Identity driven user access
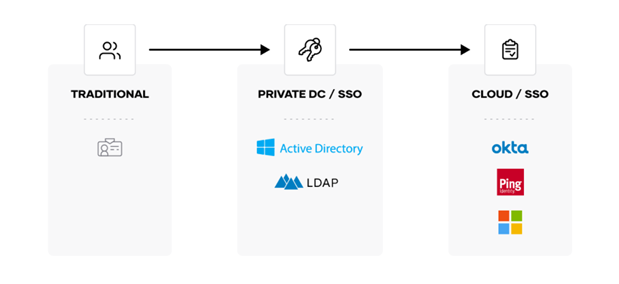
Traditional solutions for safeguarding user access require distributing and managing SSH keys, VPN credentials, and bastion hosts. This approach creates risks around credential sprawl, network exposure, and requires substantial manual effort to maintain.
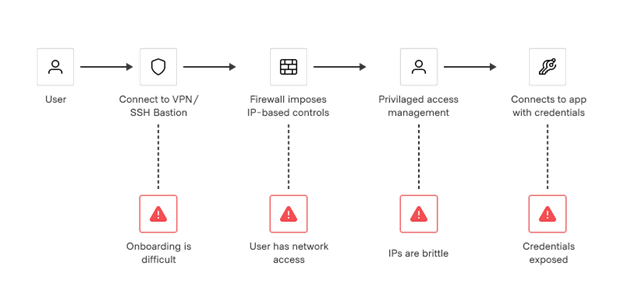
Traditional access workflows are manual and introduce multiple points of vulnerability
Modern approaches for human-to-machine access should rely on verifying the identity of the user, confirm and authorize access, establish permissions to the end system, and be automated.
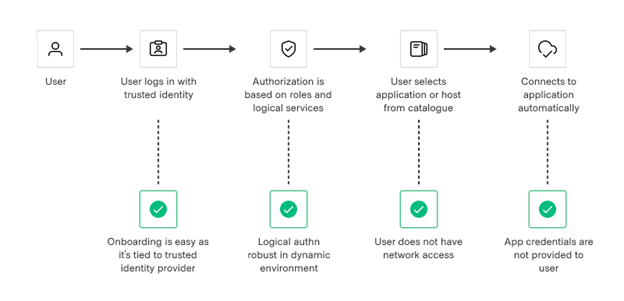
Modern access workflows are automated and use identity as their foundation
HashiCorp Boundary solves modern access challenges. Boundary is a secure remote access solution that provides an easy way to safeguard access to applications and critical systems with fine-grained authorizations based on trusted identities. Boundary governs access across clouds, local datacenters, and low-trust networks, without exposing the underlying network.
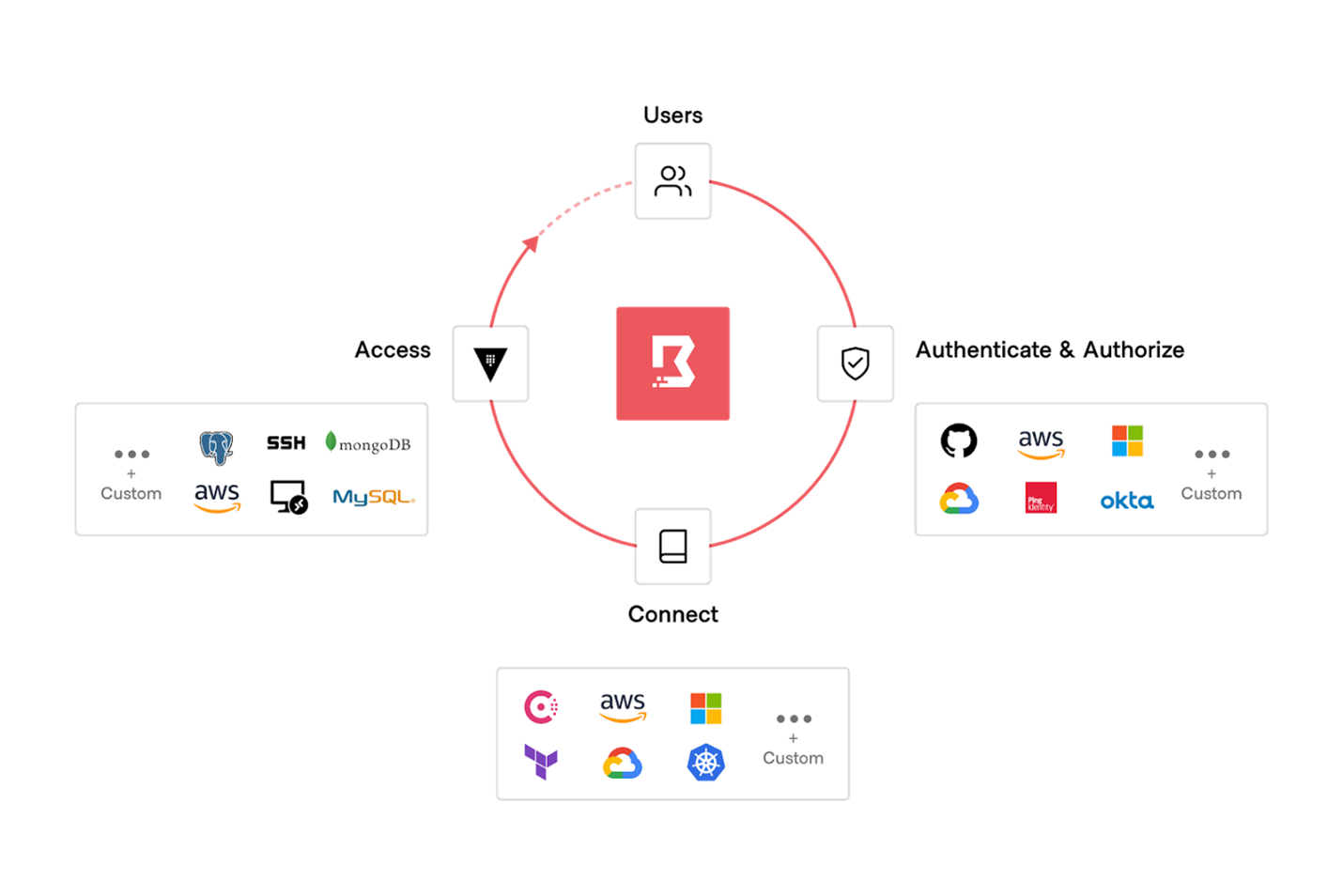
HashiCorp Boundary delivers simple and secure remote access to any system anywhere, based on user identity
Users can authenticate to Boundary using their identity provider of choice and be tightly authorized to perform actions on a dynamic set of targets. Additionally, the user can be granted just-in-time access to connect to those targets via dynamic credentials provided by Vault.
Identity based security and Zero Trust frameworks and workflows
Security in the hybrid cloud is being recast from static and network centric to dynamic and identity-based. The recent Executive Order on Improving the Nation’s Cybersecurity (May 12, 2021), emphasizes the importance and critical nature of adopting zero trust approaches, environments, and workflows.
The transition from traditional on-premises datacenters to dynamic, compliant hybrid cloud infrastructure platforms is complex and introduces new security challenges. As the IC moves to the hybrid/multi cloud (C2E) managing access at scale becomes brittle and complex. This shift requires a different approach to security and a different trust model; one that trusts nothing and authenticates and authorizes everything. Zero trust security is predicated on securing everything based on trusted identities and is an essential component of secure hybrid cloud adoption.
Adopting Zero Trust Security
HashiCorp has outlined six fundamental steps organizations can take to enable a zero trust approach and increase their zero trust security posture. For more information please refer to the Whitepaper: Enabling Zero Trust Security in the Public Sector.
- Step 1: Centrally Store and Protect Secrets/Credentials.
- Step 2: Leverage Dynamic Credentials – Dynamic secrets eliminate the ability for attackers to steal credentials as they don’t exist until requested and are time bound.
- Step 3: Replace Perimeter Based Security with Identity Based Security – Adopt an identity-based security approach that focuses on the authenticated identity of a resource, individual, or application/service.
- Step 4: Encrypt Everything – Encrypting data in transit and at rest.
- Step 5: Authenticate and Authorize all Network Traffic – Identity based machine-to-machine access must enforce authentication between services/applications.
- Step 6: Multi-Factor Authentication (MFA).
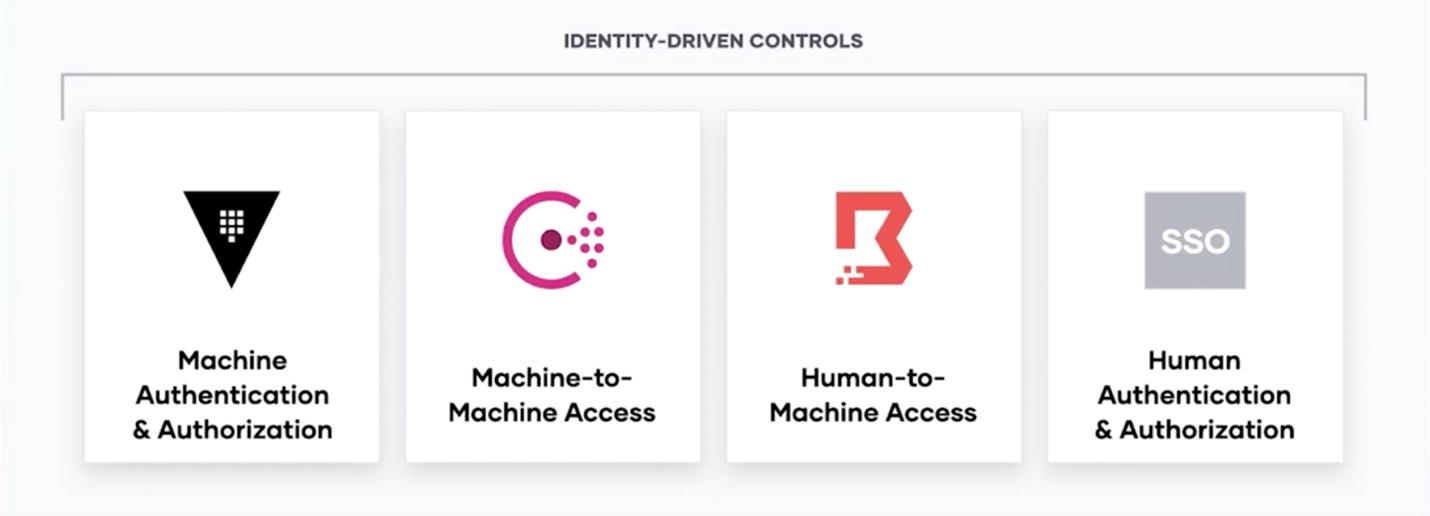
The common thread through all six steps for implementing zero trust security is identity. Based on this, there are four foundational categories for identity-driven controls and zero trust security:
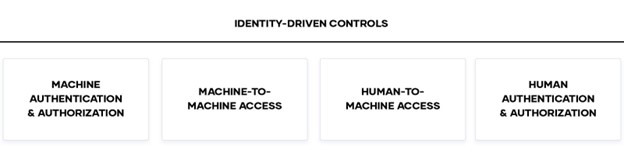
At HashiCorp, our security model is predicated on the principle of identity based access and security. HashiCorp offerings can address each pillar and make zero trust security truly work:
- Machine Authentication & Authorization: HashiCorp Vault enables practitioners and organizations, based on identity, to centrally secure, store, access, and distribute static and dynamic secrets like tokens, passwords, certificates, and encryption keys across any public or private cloud environment.
- Machine-to-Machine Access: HashiCorp Consul enables machine-to-machine access by enforcing identity based authentication between applications and ensuring only the right machines are talking to each other.
- Human Access and Authorization: IC organizations use different identity platforms for federated systems of record. HashiCorp products have deep integration with the leading identity providers.
- Human-to-Machine Access: HashiCorp Boundary provides simple, identity based, secure remote access to securely access dynamic hosts and services without managing credentials or IPs, or exposing your network.
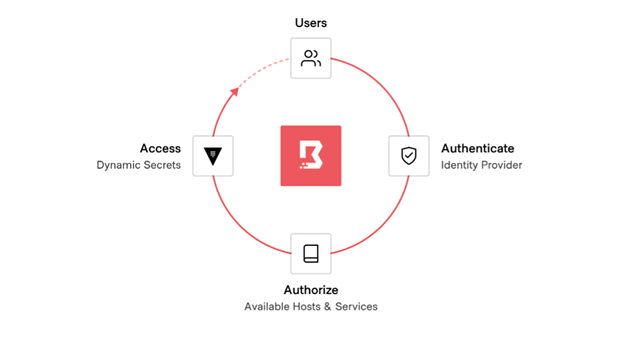
HashiCorp’s approach to identity-based security and access provides a solid foundation for organizations to safely migrate and secure their infrastructure, applications, and data as they adopt hybrid/multi-cloud.
To learn more about how HashiCorp can help on this Zero Trust journey please refer to our White Paper: Unlocking the Cloud Operating Model: Security
Conclusion
HashiCorp is secure platform automation for the hybrid/multi-cloud era.
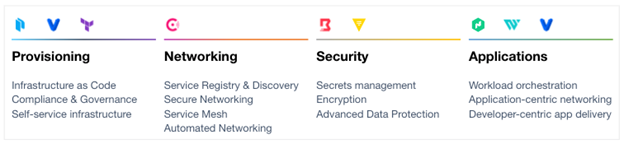
To practically adopt a secure multi-platform approach that successfully leverages hybrid/multi cloud and enable the successful adoption of the Intelligence Community Commercial Cloud Enterprise (C2E) environment, a secure cloud operating model is an inevitable shift for enterprises. The HashiCorp suite of tools seeks to provide solutions for each layer of the cloud operating model and solve complex infrastructure challenges to meet mission needs.
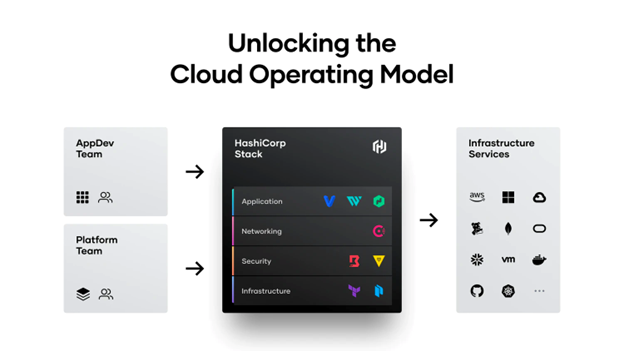
HashiCorp and our cloud infrastructure automation tooling are purposefully built to help complex organizations successfully deliver mission outcomes, securely, and at scale across any platform.
Additional Information:
Whitepaper: Unlocking the Cloud Operating Model
White Paper: Unlocking the Cloud Operating Model: Security
Whitepaper: A Leadership Guide to Multi-Cloud Success for the Intelligence Community
Whitepaper: Enabling Zero Trust Security in the Public Sector
Intelligence Community News Articles by HashiCorp:
- The Multi-Cloud Era is Here
- Getting Started with Zero Trust Security
- Enabling Zero Trust at the Application Layer
- Enabling Zero Trust at the Device/Machine and Human/User Layers
- A Leadership Guide – Multi-Cloud Success for the Intelligence Community
- A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community
About HashiCorp
HashiCorp is the leader in multi-cloud infrastructure automation software. The HashiCorp software suite enables organizations to adopt consistent workflows to provision, secure, connect, and run any infrastructure for any application. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, and Nomad are downloaded tens of millions of times each year and are broadly adopted by the Global 2000. Enterprise versions of these products enhance the open source tools with features that promote collaboration, operations, governance, and multi-data center functionality. The company is headquartered in San Francisco and backed by Mayfield, GGV Capital, Redpoint Ventures, True Ventures, IVP, and Bessemer Venture Partners. For more information, visit www.hashicorp.com or follow HashiCorp on Twitter @HashiCorp.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.








