Just Start! – Implementing Zero Trust Workflows for the Intelligence Community

From IC Insider HashiCorp
By:
Greg Thomas, Systems Engineer
Timothy J. Olson, Systems Engineer
Jarrod Gazarek, National Security Group Lead
“Just start” is an axiom commonly used when wrestling with new ideas and approaches. As we continue to face increasing threats and escalating cyber attacks, securing hybrid/multi-cloud (cloud) operational environments is critical for the Intelligence Community (IC). The challenges faced with securing an enterprise data center as well as a single cloud (C2S) is difficult and now with the era of hybrid cloud environments (Commercial Cloud Enterprise (C2E)) it’s not only essential it’s increasingly complex and challenging. This article will focus on how to apply the axiom by implementing an approach to establish secure foundations and practices for the effective adoption of hybrid cloud. For additional information on overall approaches and considerations on Securing hybrid cloud environments please refer to A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community (IC News, August 14, 2022).
With C2E, the IC is currently evaluating and undergoing initiatives to adopt effective digital transformation practices. This means adopting industrialized workflows that can securely deliver new business and mission objectives quickly, on demand, and at a very large scale across any operational environment (see IC News, July 6, 2022): A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community). This makes establishing effective zero trust based security approaches and practices for secure operations for complex hybrid/multi cloud environments, like C2E, critical and time sensitive. Governance/Security is one of the four key challenges (Skills gap, Scalability, Governance, and Untenable Costs) discussed in a previous article, A Leadership Guide – Multi-Cloud Success for the Intelligence Community (IC News, April 18, 2022).
As discussed in previous articles, establishing a platform approach is instrumental in achieving the maximum benefits from a hybrid cloud and key from a security perspective. Effective platform teams deliver infrastructure, runtimes, services, standardized workflows, enabling secure operational cloud adoption. Organizations often position their hybrid cloud platform as a product, a key principle of user-centered design.
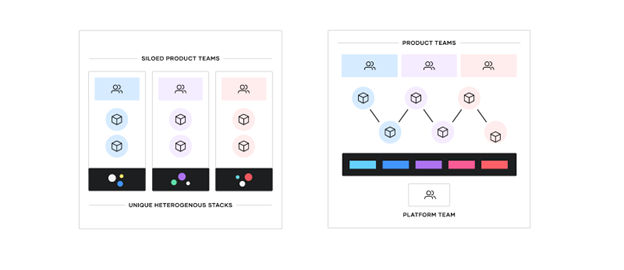
The shift to hybrid/multi-cloud environments (C2E) is enabling enterprises to offer a wider range of services and resources. As a result, the challenge for most enterprises is how to consistently deliver mission applications rapidly and securely across any operational platform. Compounding this challenge, the underlying IT primitives have expanded encompassing disparate, complex, operational models.
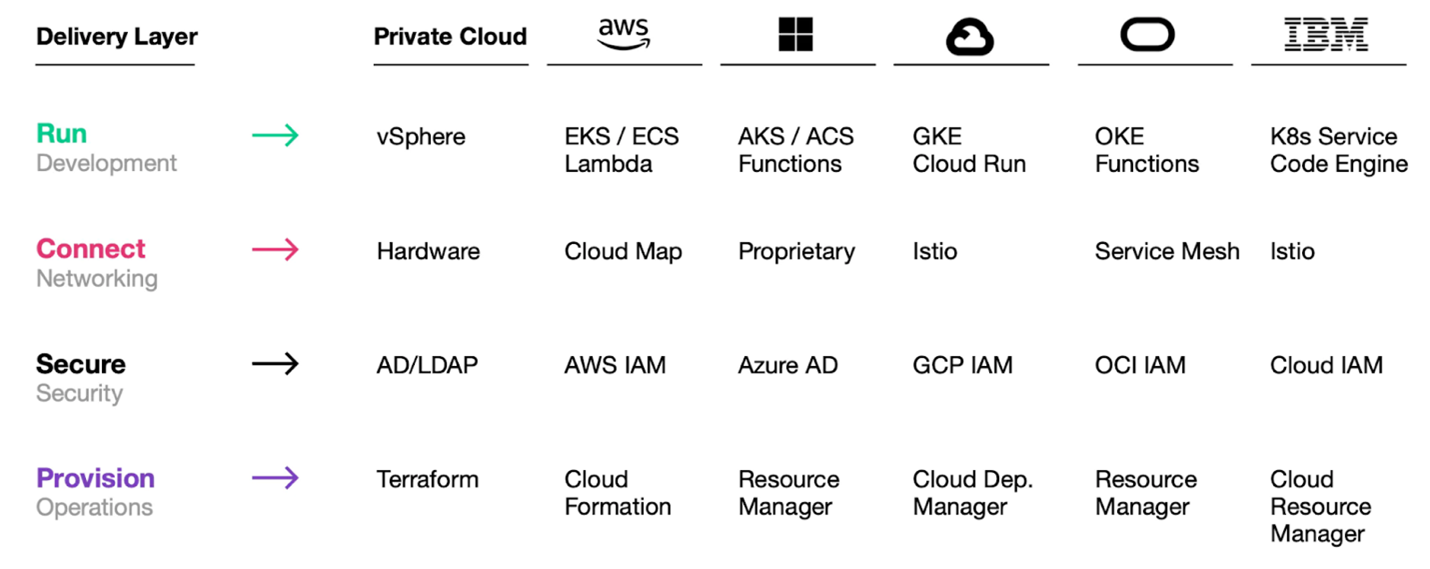
This shift is highly disruptive to traditional security models. For hybrid cloud computing to be effective and adaptable for mission deployments there needs to be consistent secure approaches and workflows that are reused at scale across multiple environments and cloud providers. Fundamentally, this requires:
- Compliant Platforms / Infrastructure with consistent Secure Workflows
- Secure Platform Secrets (sensitive data/information) Management
- Dynamic Secrets and Encryption everywhere
- Secure Service/Application level connectivity
- Identity Based Security and Identity Driven Access
- Zero Trust Frameworks and Workflows
Let’s Get Started: Security Considerations for Implementing Zero Trust
Adoption of the practices, introduced above, establishes shared service layers across the hybrid/multi-cloud and presents an industrialized process for secure application delivery, all while taking advantage of the dynamic nature of each layer of the cloud. The platform team’s responsibility is to keep the platform stable, resilient, performant, and secure. Getting started with establishing and implementing secure hybrid/multi-cloud operational environments begins here:
- Establish Secure Platform Secrets (sensitive data/information) Management
- Use Dynamic Secrets and Encryption everywhere
- Enable Identity Based Security and Identity Driven Access
- Implement Zero Trust Frameworks and Workflows
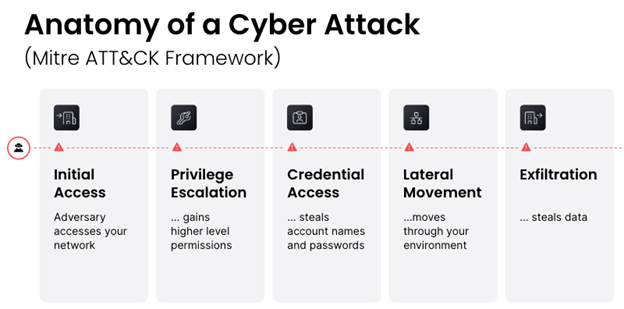
In a stepwise fashion, implementing these foundational approaches establishes safeguards and a strengthened security posture to help protect against “bad actors” and key aspects of the well documented MITRE ATT&CK Pattern (Initial Access, Privilege Escalation, Credential Access, Lateral Movement, and Exfil), thereby enabling mission success via centralized secrets management and zero trust workflows built on a heightened security framework.
Set the Foundation: Establishing Centralized Secrets Management
Secrets management is foundational for building and establishing zero trust based secure hybrid cloud operational environments and directly addresses the challenges and issues of secrets sprawl. Secrets are sensitive information and consist of anything that gives or provides access to a system or allows authentication or authorization of yourself and associated applications. Examples would be username or password, an API token, credentials, certs/TLS certificates, keys, etc.
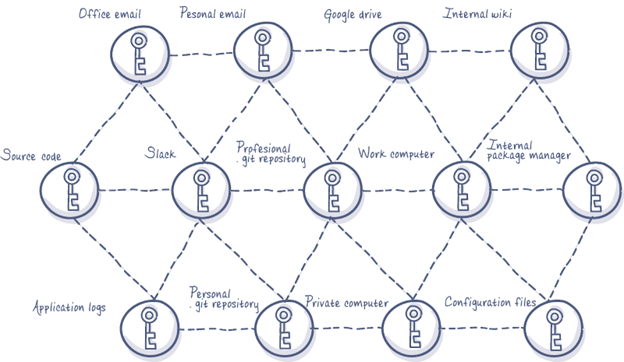
Secret Sprawl Exposes and Increases Attack Surface Increasing Vulnerability and RIck
Image from hashnode.com: What is secret sprawl, why it’s dangerous, and how developers can prevent it? Jun 4, 2020
Secrets are very sensitive and must be protected, controlled, managed, and audited. Secret sprawl is the resulting distribution of this sensitive information. Secrets tend to be littered and scattered about our infrastructure, clouds, and workflows. This could be password lists on a spreadsheet, a database username and password that’s hard-coded into the source code of an application, in plaintext in a configuration file, or in plaintext in version control. Sensitive, potentially compromising information is sprawled all over our infrastructure in different places.
This presents high levels of exposure significantly increasing risk and vulnerabilities. The challenges with sprawl include:
- Lack of visibility. We don’t actually know what’s out there and where secrets are used, stored, and accessed. It’s very difficult to track what’s in source code, what’s in a repository, or what’s in a Version Control System (VCS).
- Limited access control and management. Most applications and systems are not designed for secret management. Many times a Wiki or Dropbox or a version control repo have no idea they are storing secrets. There are little to no controls, management, or maintaining fine-grain audit logs of what credentials are accessed and distributed.
- Limited recourse (break glass scenario), remediation, recovery, in event of a breach. We often don’t know where the compromised information came from (in the source code? Hardcoded? In a config file somewhere?) making it very difficult to stop and remediate this breach. Following a breach there is often a complex process to address, implement, and orchestrate changes.
Securing platform secrets (Secret Management) addresses and solves secret sprawl and the associated risks.
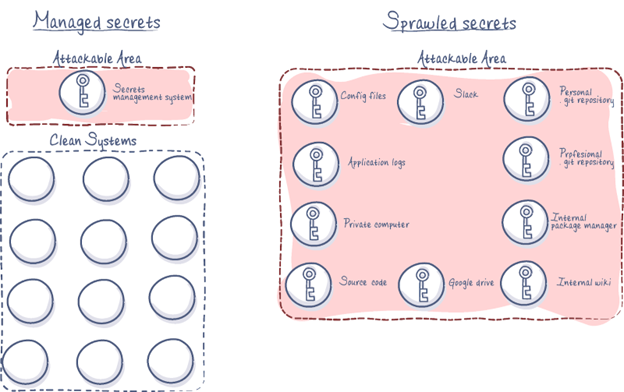
Encrypted Centralized Secrets Management Reduces Vulnerability and Risk
Image from: Hashnode.com
STEP 1: Secure Platform Secrets – Manage secrets and implement advanced data protection
The first level and initial starting point is centralization. Having a single central service or location for secrets where they are tightly access-controlled, tightly audited, encrypted, and time bound, is key for securing hybrid clouds and multi-platform operational environments.
Vault enables organizations to manage secrets, protect sensitive data, and control access to conform to relevant compliance frameworks across operational platforms. Vault is identity based (key to enabling zero trust). Vault authenticates these identities and uses them as a system of record to manage and enforce access to secrets and systems.
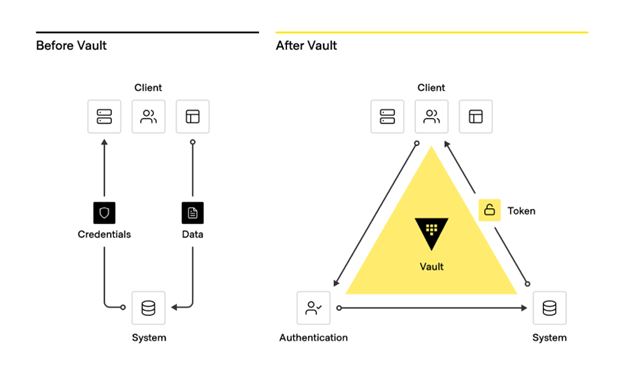
From traditional secrets workflow to modern secrets management with Vault
Vault Enterprise key capabilities:
- Manage secrets and protect sensitive data: Vault centrally stores, accesses, and deploys secrets across applications, systems, and platforms/infrastructure.
- Protect critical systems and customer data: Reduce the risk of breaches and data exposure with identity-based security automation and encrypting and securing application data (Encryption-as-a-Service) with one centralized workflow.
- Advanced auditing and reporting: Every operation with Vault is an API request/response and Vault audit logs contain every authenticated interaction.
STEP 2: Use Dynamic Secrets and Encryption Everywhere (Encryption as a Service)
Many organizations have credentials hard coded in source code, littered throughout configuration files, embedded in configuration management tools, stored in plaintext in version control systems (VCS), wikis, and shared volumes, this is an issue known as Secret Sprawl. Establishing a centralized Secrets Management solution addresses this challenge. Creating automated short lived dynamic credentials across hybrid cloud and multi-platform operational environments enhances the overall security posture and greatly reduces risks, and can revoke all secrets in the event of a breach or attack.
Dynamic Secrets are generated on demand, which are unique to a client (user, machine/device, VM, container/Pod, application, etc.), time-based access credentials which are dynamically based on policies and revoke access when the lease expires. Instead of a static secret, which is defined ahead of time, usually long lived, and then shared, dynamic secrets don’t exist until requested and then expire after a defined (usually short) time to live (TTL). Vault associates each dynamic secret with a lease and automatically destroys the credentials when the lease expires. Vault supports dynamic secrets with a wide range of systems and is easily extensible with plugins.
Protecting sensitive data across clouds, applications, and systems is challenging. Securely handling data such as social security numbers, credit card numbers, and other types of compliance-regulated information can be complicated. Centralized secrets management enables the ability to Encrypt and Tokenize application data with Vault.
Vault’s various data protection capabilities are designed to satisfy a full range of security and usability needs such as providing traditional data encryption, format preserving encryption (FPE), data masking, data tokenization, centralized key management, and much more to simplify protecting data in transit and at rest across hybrid clouds, platforms, and data centers.
Vault can provide a central, standardized, encryption as a service (EaaS) as a consistent API for key management and cryptography. The Vault API exposes cryptographic operations to secure sensitive data without exposing encryption keys. Vault also can act as a certificate authority (root or intermediary) to provide dynamic short-lived certificates to secure communications with SSL/TLS.
Vault enables IC organizations to provide secrets management and data encryption services across platforms, applications, and mission teams.
STEP 3: Enabling Identity-based Security and identity driven access (enabling zero trust)
Establishing and managing identity is complex.
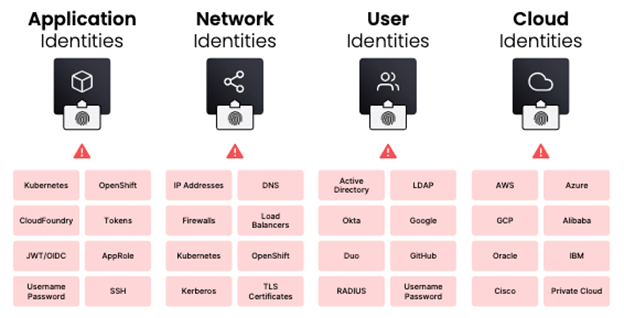
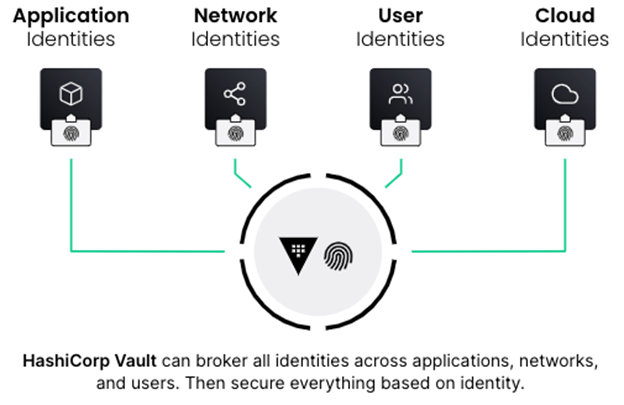
Managing access to secrets in a hybrid/multi-cloud world consists of two primary user types: humans and machines. Managing secrets for humans is well established. Machines are a different issue as they can include servers, virtual machines, containers, applications, microservices, and more, all potentially needing access to different systems and secrets. When it comes to managing secrets with machines in a hybrid/multi-cloud environment, the dynamic, identity based, nature of HashiCorp Vault comes to the forefront.
Vault’s identity system is an essential capability that enables brokering identities between different platforms into unified identities to allow applications to work across platform boundaries. Whether a machine or user is looking to create and distribute organizational secrets, Vault solves managing this access based on trusted identities.
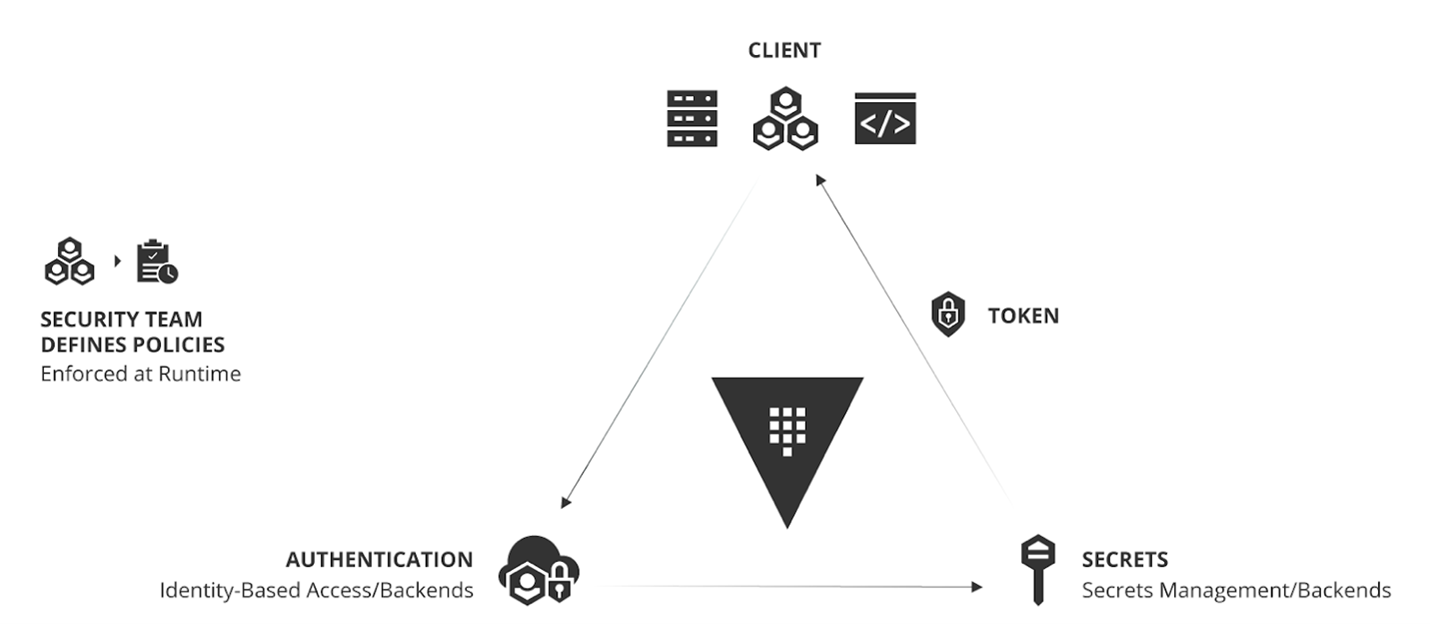
Operating Model for Identity-based Security and Secrets Management
The adoption of this operating model for identity-based security and secrets management with Vault is an inevitable shift for enterprises aiming to rationalize and adopt hybrid/multi-cloud security.
Sentinel – Policy as Code Framework for HashiCorp Enterprise Products
HashiCorp Sentinel is a Policy as Code (PaC) framework to enable logic-based policy decisions that can be extended to source external information to make decisions. Sentinel provides these key advantages when deploying secure platforms:
- Embedded: Enable policy enforcement in the data path to actively reject violating behavior instead of passively detecting.
- Multiple enforcement levels: Allow policy writers to warn or reject offending behavior.
- External information: Source external information to make holistic policy decisions.
- Hybrid/Multi-cloud compatible: Ensure infrastructure changes are within mission and regulatory policy across every infrastructure provider.
STEP 4: Zero Trust Capabilities in Action
In February 2021 the National Security Agency published, “Embracing a Zero Trust Security Model.” The executive summary clearly articulates the four phases of Zero Trust Implementation: Preparation, Basic, Intermediate and Advanced. While some have attempted and struggled, others have followed the guidelines and moved strategically through the phases. They have done so by working with industry and government to disrupt, collaborate, and innovate. This series of articles will describe practical ways to get started and move through each phase.
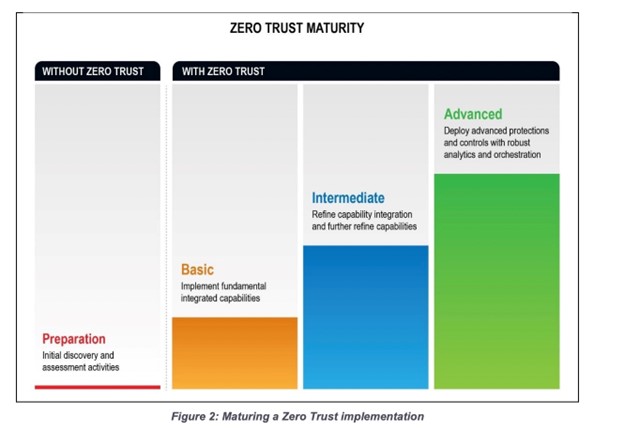
Each article in this three-part series will share a real world example of success based on the model. As we walk through the series, starting with Zero Trust Implementation steps above, these steps mitigate elements of the MITRE ATT&CK Pattern. Implementing the above steps initially addresses the Initial Access, Privilege Escalation, Credential Access, and enables centralized secrets management and zero trust workflows built on that heightened security framework.
Compromised User Credentials
This guide offers several examples of zero trust in use. The first is how to mitigate the risk of compromised user credentials. During the preparation phase, many organizations conduct secret discovery, but often only for traditional Privileged Access Management (PAM) or usernames and passwords. A secret is anything that could be used to compromise a system. An identity provider (IDP), for example, is a secret. Centralized management of secrets is necessary to secure and maintain control and compliance in government with FIPS 140-2 and data encryption at rest and in transit. It has been widely adopted in the financial sectors and many other leading industries. Secret management solves the problem of secret sprawl for the government. Vault is purposely built to solve this problem on any runtime or platform.
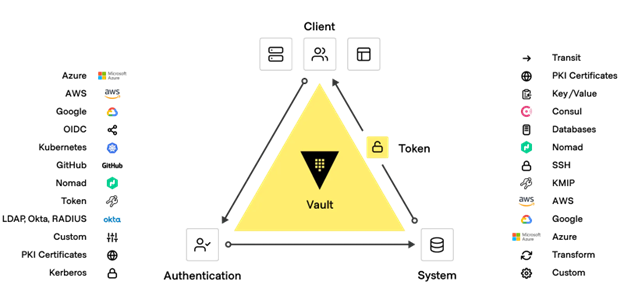
The Universal Principles of Zero Trust are designed into Vault – advanced security capabilities do not need to be bolted on. Vault comes with the Advanced Data Protection module, providing encryption as a service (EaaS) and Key Management Interoperability Protocol (KMIP) capabilities. Policy enforcement, Multi Factor authentication, FIPS 140-2, are also in the core workflow for Vault.
Implement Fundamental Zero Trust Capabilities
After a holistic secrets discovery process is complete and some basics are planned, the next step is to select a secrets management platform that is built on the Universal Principles of Zero Trust and runs on any platform or runtime including Cloud Service Providers (CSP). Next, start small, and learn to store “Your First Secret.” Once you understand the basics, set up a solutions session to scope where your agency or department’s gaps are. Secret sprawl, as warned in the Supply Chain Guidance, often leads to hacks like those described in “FBI, CISA, and NSA Reveal How Hackers Targeted a Defense Industrial Base Organization” and “VA Investigates breach after federal contractor publishes source code”, two recently published reports.
HashiCorp Learn provides clear examples available for testing. The HashiCorp Federal Solutions Engineering team is available to work with you to create a proof-of-concept test environment and assist you in learning more about secrets management. The best thing you can do is get started. Secret sprawl is a large vulnerability that introduces significant risk to your environment; if you do not know where to find your secrets or how to protect them, you need to start. In the next article we will address how to stop Lateral Movement based on this model.
Conclusion
HashiCorp is secure platform automation for the hybrid/multi-cloud era. Many organizations implement this foundational approach to address some key use cases/workflows:
- Support Teleworking
- Protect Critical Resources
- Reduce Vulnerabilities and Threats
- Limit Exposure and Breaches
- Improve Incident Response/Recovery
- Protect Sensitive Data
- Improve Visibility
Implementing centralized secrets management and establishing core zero trust workflows is often the foundational step for more advanced workflows, securing automated deployments, and accelerating secure mission deployments.
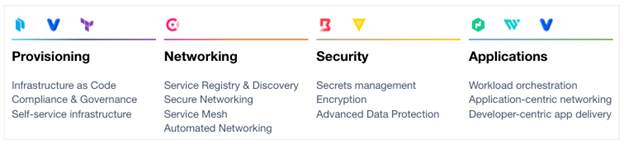
To “Just Start” and practically adopt a secure multi-platform approach that successfully leverages hybrid/multi cloud and enable the successful adoption of the Intelligence Community Commercial Cloud Enterprise (C2E) environment, a Secure Cloud Operating Model is an inevitable shift for enterprises. The HashiCorp suite of tools seeks to provide solutions for each layer of the cloud operating model and solve complex infrastructure challenges to meet mission needs.
HashiCorp and our cloud infrastructure automation tooling are purposefully built to help complex organizations successfully deliver mission outcomes, securely, and at scale across any platform.
Additional Information:
Whitepaper: Unlocking the Cloud Operating Model
White Paper: Unlocking the Cloud Operating Model: Security
Whitepaper: A Leadership Guide to Multi-Cloud Success for the Intelligence Community
Whitepaper: Enabling Zero Trust Security in the Public Sector
Intelligence Community News Articles by HashiCorp:
- The Multi-Cloud Era is Here
- Getting Started with Zero Trust Security
- Enabling Zero Trust at the Application Layer
- Enabling Zero Trust at the Device/Machine and Human/User Layers
- A Leadership Guide – Multi-Cloud Success for the Intelligence Community
- A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community
- A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community
About HashiCorp
HashiCorp is the leader in multi-cloud infrastructure automation software. The HashiCorp software suite enables organizations to adopt consistent workflows to provision, secure, connect, and run any infrastructure for any application. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, and Nomad are downloaded tens of millions of times each year and are broadly adopted by the Global 2000. Enterprise versions of these products enhance the open source tools with features that promote collaboration, operations, governance, and multi-data center functionality. The company is headquartered in San Francisco and backed by Mayfield, GGV Capital, Redpoint Ventures, True Ventures, IVP, and Bessemer Venture Partners. For more information, visit www.hashicorp.com or follow HashiCorp on Twitter @HashiCorp.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.








