From IC Insider HashiCorp
As IC and DoD organizations embark on their IT modernization strategies, they will face various hybrid/multi-cloud challenges, which includes an exponential increase in complexity to deliver applications. With multiple Cloud Service Providers now available, it will take time for the workforce to adopt and develop skills to manage new cloud technologies.
Many public sector organizations, such as those within the Department of Defense and the Intelligence Community choose to innovate with HashiCorp Federal. HashiCorp’s products are cloud/platform-agnostic tools that offer organizations a methodology to seamlessly optimize their existing workflows and facilitate their hybrid/multi-cloud strategy by making it easier to deploy applications across on-prem and multiple cloud platforms at scale.
This discussion will expand on topics from the article: Getting Started with Zero Trust Security. The adoption of Zero Trust can be challenging as Zero Trust principles and approaches are usually unique for every environment and often many organizations are faced with the dilemma of how to start adopting zero trust. This article will expand on those foundational principles and discuss the challenge of Application connectivity or “Enabling Zero Trust at the Application Layer.”
The shift to networking dynamic infrastructure
The move to more dynamic hybrid/multi-cloud environments presents challenges with the measures previously taken to secure traditional/private datacenters. This dynamic environment, whether on prem, cloud based, or both, necessitates the adoption of identity based security and a fundamental shift from traditional IP-based perimeters and access. Identity based security is key to adopting Zero Trust for Application/Services based connectivity.
Traditional Data Center Dynamic Environment
- Networks, Firewalls – Dynamic access and networking
- IP-based perimeter and security – Identity Based Security
- HSMs, SIEM software – Software defined access and controls
- Physical access and restrictions – Multiple clouds and private datacenters
- Static IPs, primarily north-south traffic – Dynamic IPs, primarily east-west traffic
- Protected by perimeter security – No clear network perimeters
- Coarse grained network segments – Ephemeral containers, Immutable
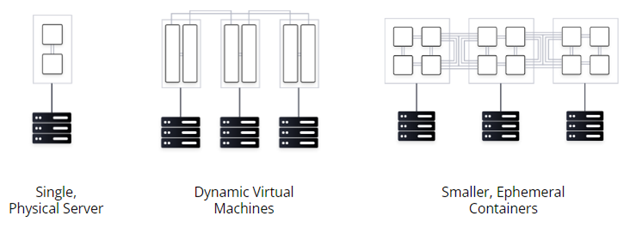
In a traditional network, applications are connected and secured by a fleet of network infrastructure, such as routers, switches, load balancers and firewalls. Organizations focus on managing the traffic flowing in and out of the datacenter (also known as north-south traffic). The network is protected by coarse-grained network segments and is IP centric. The network operation processes are normally ticket-based and manual. For example, it could easily take many days or weeks to update a chain of network infrastructure devices in order to launch a new application.
The trend of application modernization, compounding with cloud adoption has shifted the underlying networking layer from host-based static networking to service-based dynamic networking.
In today’s multi-platform, multi-cloud network:
- Microservices are running on ephemeral containers with dynamic IPs.
- Environments with duplicate IP Address spaces have grown in frequency.
- The explosion of service-to-service communication (also known as east-west traffic) results in dynamic, complex traffic patterns and potential vulnerabilities from lateral movement attacks.
- The public clouds blur the boundary of network perimeters, presenting a new set of security risks.
As the network becomes larger and more dynamic, it puts pressure on networking and security teams to keep pace with more changes to existing network infrastructure. These teams often cannot keep up with the increasing demand, and their manual approach to network operations undermines the agility and security posture of application teams.
The shift in Application/Services deployment approaches places even greater complexities on securing the environment as the need to support multiple operational approaches and platforms grows. The adoption of cloud and microservices means organizations shift away from static connectivity between services and ticket-driven processes to update network middleware to services discovered and connected with centralized policies and a zero trust network enforced by identity based security.
An IP centric approach as a security control point is challenged by the demands of a dynamic/ephemeral environment as managing access across multiple dynamic platforms and associated IP’s at scale becomes brittle and complex. Securing infrastructure, data, and access becomes increasingly difficult across clouds and on-premises datacenters, requiring overhead and expertise.
This shift requires a different trust model. Zero Trust for Application connectivity trusts nothing and authenticates and authorizes everything. Machine-to-machine access (application connectivity) is a core element of a hybrid/multi-cloud-first organization. Machine-to-machine access must enforce authentication between applications and ensure that only the right machines are securely talking to each other. This can be implemented through the use of a platform agnostic, multi-environment/multi-data center, federated, service connectivity solution that creates a consistent platform for modern application networking and security with identity-based authorization, Layer 7 (L7) traffic management, and service-to-service encryption (essentially a Zero Trust based federated super service mesh).
HashiCorp Consul
Consul is a service to service connectivity (or often referred to as application level networking) solution providing a full featured control plane with service discovery, configuration, and segmentation functionality. Each of these features can be used individually as needed, or they can be used together to build a full service mesh. Designed to solve the rising networking and security challenges for dynamic infrastructure and enable progressive delivery practices, Consul provides a hybrid/multi-cloud software service connectivity platform to discover, connect, and secure services.
Consul takes a different approach to service connectivity/application networking by:
- Abstracting (decoupling) the operation from IP address to service level based on identity.
- Providing a central shared service workflow to locate the dynamic location of services.
- Enabling service discovery to allow services to register, discover, and connect with each other directly.
- Driving automation to eliminate the operational burden of manually updating network infrastructure.
- Provides a service connectivity solution to simplify service networking by shifting naming abstraction, routing, authorization and other networking functionality from a central networking infrastructure layer to the endpoints.
- Being platform-agnostic, which allows IT teams to maintain a single networking workflow to networking across different runtime platforms, public cloud or private clouds.
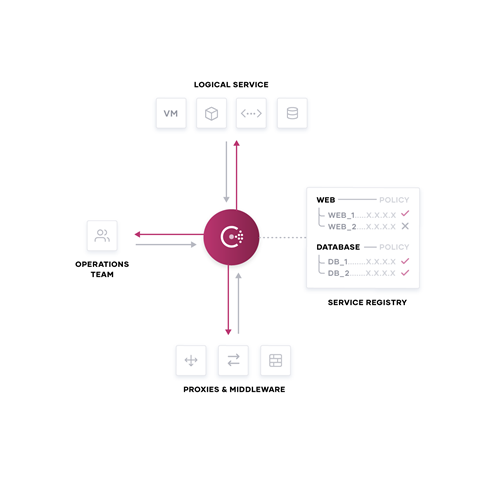
Consul enables hybrid/multi-cloud application connectivity automation with a central shared registry to discover, connect and secure services across any runtime platform and cloud. With service discovery, services can dynamically locate any application or services to simplify network connectivity and routing. With network middleware automation, service changes trigger dynamic reconfiguration automatically to load balancers and firewalls. And with agnostic, multi-platform, service mesh, consistent end-to-end identity based security is enforced and applied to services across a heterogeneous environment.
- Shared registry to decouple from IP addresses with service name as identity.
- API driven to codify and automate service definitions, health checks, authorization policies and more.
- Run and connect anywhere to connect services from Kubernetes to VMs, containers to clouds.
- Securely connect and observe applications using service discovery and service mesh patterns.
- Automate service networking across multiple run time platforms and clouds.
- Discover and securely connect any service on any runtime.
- Central control plane to enable multi-cloud networking for dynamic environments.
- Adopt a central service registry to provide a real-time directory of running applications.
- Service registry and discovery to improve resiliency enable cloud and application teams to improve resiliency with visibility into running applications and services and upon failure re-route healthy service traffic.
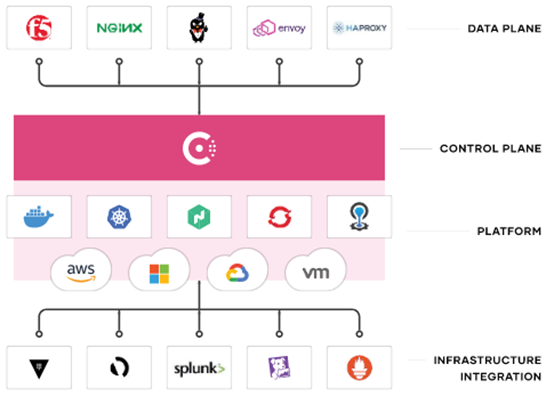
With Consul, organizations can improve security and apply key Zero Trust principles across service-to-service communications and run a consistent platform for modern application connectivity (networking) and security with identity-based authorization, L7 traffic management, and service-to-service encryption.
Key Principles of Zero Trust:
- Identity driven
- Mutually authenticated
- Authorized
- Time-bound
- Encrypted Transit
- Audited & logged
- Data Protection
- Encrypted Transit
- Encrypted Data at Rest
Consul enables adoption of Zero Trust at the Application Layer (machine to machine access) to reduce risk and cost. Consul provides secure service-to-service traffic with identity driven controls to ensure zero trust based security policies and encrypted traffic with mutual-TLS across any environment. Consul secures and encrypts connections and enables operators to define approved traffic patterns based on service/application identity. Security teams can easily enforce consistent policies with 100x fewer security rules to manage.
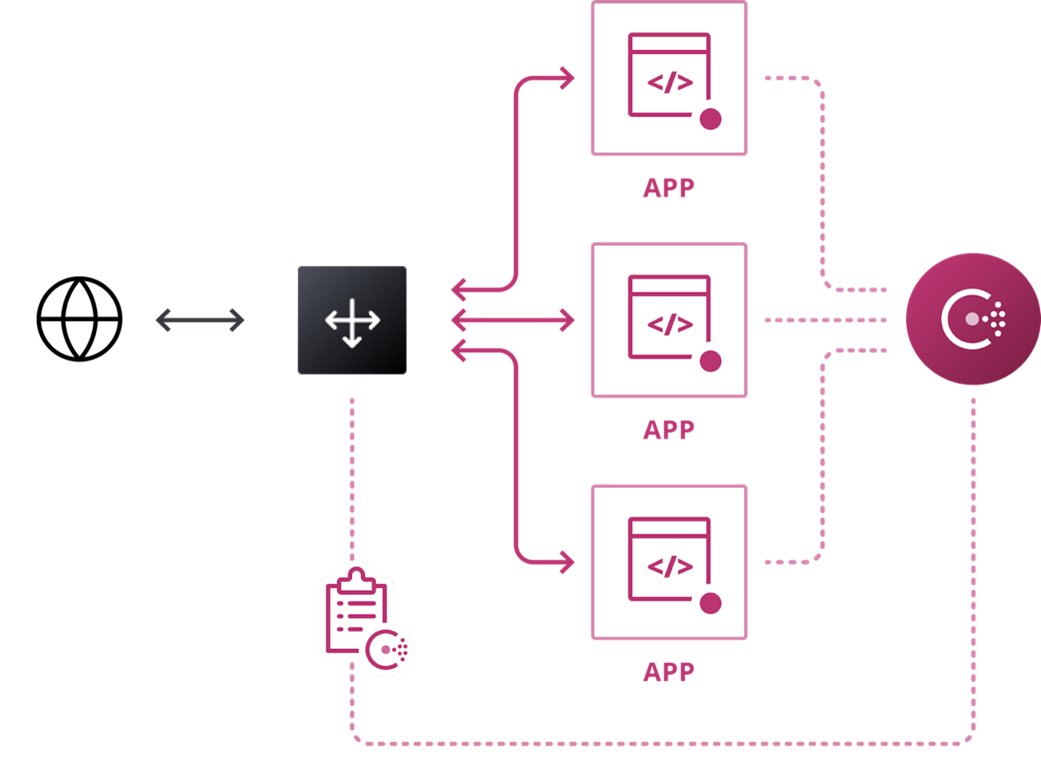
Consul improves and optimizes traditional networking infrastructure/environments (north-south traffic) using Network Infrastructure Automation to increase productivity and reduce risk and vulnerabilities. Consul knows and tracks services and can dynamically publish service changes to network middleware and automate network tasks significantly improving network efficiency while reducing costs and risk. Developers can roll out new services, scale up and down, and gracefully handle failure without operator intervention.
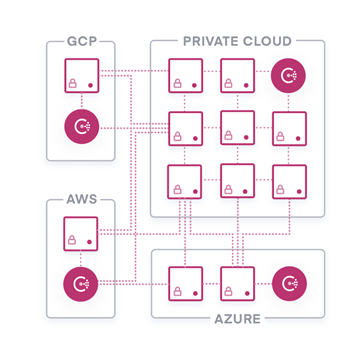
Adoption of Consul and enabling Zero Trust at the Application Layer typically follows a three-stage pattern for most organizations. First, organizations can establish a foundation of services networking with Consul using a common service registry and by providing service discovery across their hybrid/multi-cloud environments. Second, organizations can standardize on delivering a shared services approach across various operational teams to automate networking processes that were formerly manual and ticket based. Third, they can start to migrate and innovate their service networking to a service connectivity (mesh) architecture to improve agility, security, performance, reduce cost and adopt Zero Trust.
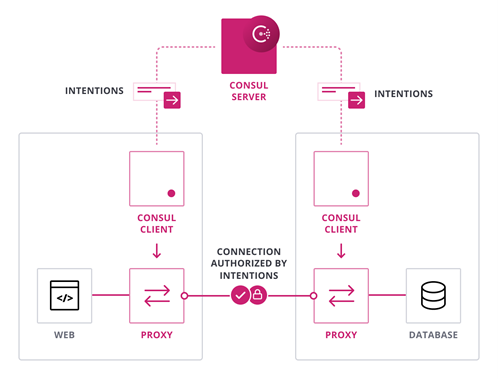
Consul enables a zero-trust network model by securing service-to-service communication with automatic mutual TLS encryption and identity-based authorization. Network operation and security teams can define the security policies through intentions with logical services (identity based) rather than IP addresses. For example, allowing web services to communicate with databases, instead of IP1 to IP2. Consul can also be integrated with HashiCorp Vault or AWS PCA for centralized PKI and certificate management.
For cross-cloud communications, Consul’s Mesh Gateway feature routes traffic to the correct endpoint on a private network without requiring expensive IPSec or MPLS connectivity.
Organizations require services networking to become more application centric, and allow organizations to bring old and new applications together in a heterogeneous way, rather than requiring an all or nothing approach involving complex cloud migration and application refactoring. Organizations want their service connectivity to be consistent across all of their workload platforms, runtimes, and environments.
For most IC and DoD enterprises, the goals of digital transformation efforts mean delivering new mission and customer value more quickly, securely, and at a very large scale. The implication for Enterprise IT then is a shift from cost optimization to speed optimization. The cloud is an inevitable part of this shift as it presents the opportunity to rapidly deploy on-demand services with limitless scale.
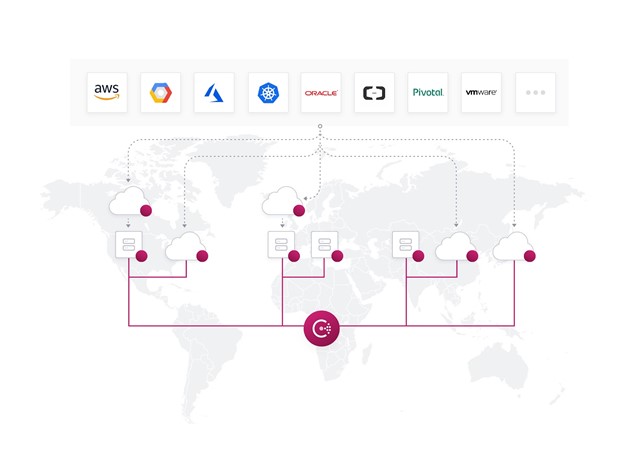
Consul enables Zero Trust at the Application Networking Layer. Discover and securely connect any service across any cloud or runtime.
HashiCorp Consul
- Identity Based
- Machine-to-Machine Identity
- Secure Service-to-service communications
- Platform / runtime agnostic
Consul’s adoption journey is a straightforward path that IC and DoD organizations can follow towards a more simplified and scalable service connectivity/application networking approach to support distributed applications with agnostic multi-cloud and multi-datacenter topologies while enabling Zero Trust at the Application Layer.
About HashiCorp
HashiCorp provides infrastructure automation software for multi-cloud environments, enabling enterprises to unlock a common cloud operating model to provision, secure, connect, and run any application on any infrastructure. HashiCorp tools allow organizations to deliver applications faster by helping enterprises transition from manual processes and ITIL practices to self-service automation and DevOps practices. For more information, visit hashicorp.com.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.








