How to Prevent Lateral Movement (Is the “Bad Actor” Already Inside?)

From IC Insider HashiCorp
By:
Greg Thomas, Systems Engineer
Timothy J. Olson, Systems Engineer
Jarrod Gazarek, National Security Group Lead
Applying Zero Trust approaches and best practices towards prevention of Lateral Movement
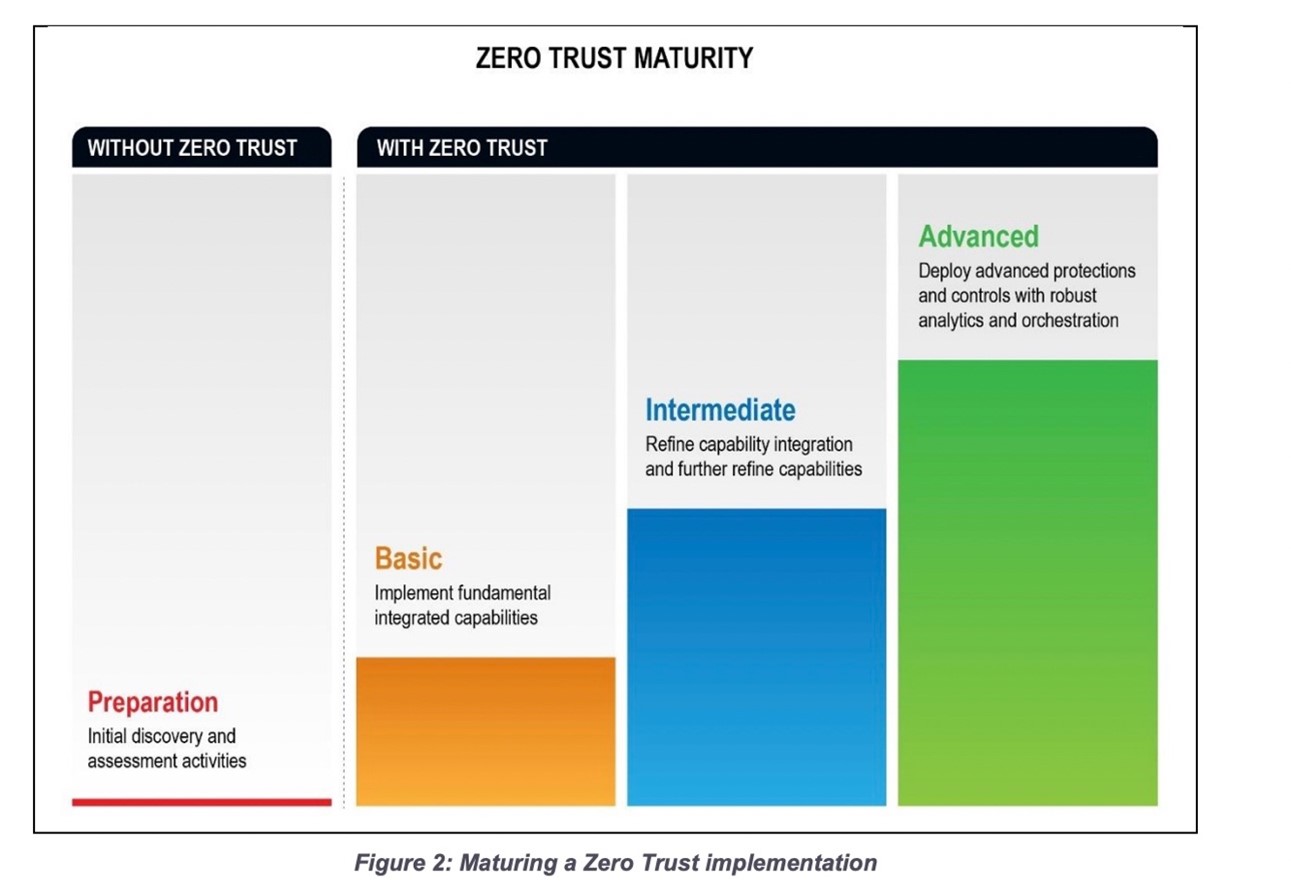
In February 2021 the National Security Agency published, “Embracing a Zero Trust Security Model.” The executive summary clearly articulates the four phases of Zero Trust Implementation: Preparation, Basic, Intermediate and Advanced. While some have attempted and struggled, others have followed the guidelines and moved strategically through the phases. They have done so by working with industry and government to disrupt, collaborate, and innovate.
This article, the second of the series, builds off of the first and describes how to prevent lateral movement. Please take a look at our previous article titled, Just Start! – Implementing Zero Trust Workflows for the Intelligence Community, for more information on how to start your Zero Trust journey.
The shift to hybrid/multi-cloud environments (C2E) is enabling enterprises to offer a wider range of services and resources. As a result, the challenge for most enterprises is how to consistently deliver mission applications rapidly and securely across any operational platform. Compounding this challenge, the underlying security and IT primitives (traditional approaches) have expanded encompassing disparate, complex, operational models, which increases the potential attack surface.
One of the foundational approaches to safeguard and protect against “bad actors” is referencing and following the well documented MITRE ATT&CK Pattern. One critical aspect of the MITRE ATT&CK Pattern is Lateral Movement, which is the act of moving through the environment from a compromised resource into an uncompromised one by exploiting the assumption that the former, and the environment, is secure.
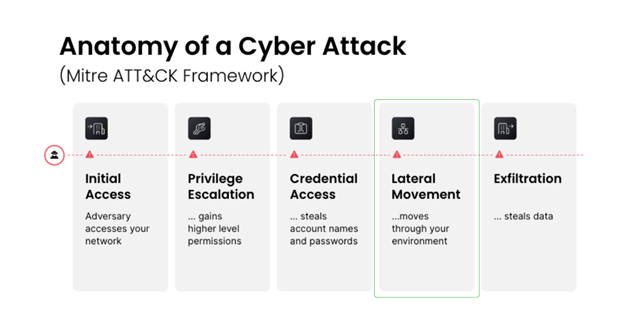
Image Source: HashiCorp
The following list describes how a “bad actor” could utilize specific and common techniques to move laterally across networks in an unauthorized fashion.
Lateral Movement Techniques
- Exploitation of Remote Services
- Internal Spear Phishing
- Lateral Tool Transfer
- Remote Service Session Hijacking
- Remote Services
- Replication Through Removable Media
- Software Deployment Tools
- Taint Shared Content
- Use Alternate Authentication Material
With these techniques, well-known and practiced, the threat of an attack is real, constant, and critically damaging to any network that falls victim. Unfortunately, these techniques are readily available, frequently used, and in easily repeatable patterns. This article will focus on mitigating steps that can, and should, be taken to protect against lateral movement. The emphasis will be on straightforward, scalable solutions that can be fully federated and implemented on any runtime or platform which prevents or stops lateral movement.
Challenge: The Traditional “Castle and Moat” Approach is Not Enough
In the traditional datacenter approach to network security, the “castle and moat” method intends to keep everything inside safe (hard exterior, squishy interior). However, if a “bad actor” manages to breach the walls of your castle (which they always do), then they will effectively have unmitigated access to all rooms and contents within the Castle. Imagine your services (applications) as rooms in this Castle and the associated data as its contents. The fact that a “bad actor” can make it into your Castle should not mean they should have free unrestricted access to any room, or each room’s contents (gain access to the internal network).

Photo by Angelo Casto on Unsplash
With the “bad actor” assumed to already be within your Castle, the entire approach is required to change in that the assumption becomes: The “bad actor” is in our Castle. How can we best mitigate their access while the guards seek to expel the intruder?
Response: PUT LOCKS ON ALL THE DOORS!
With locks on the doors, and the fact that a quartermaster issues the access keys, are two essential parts of mitigating “bad actor” access, while optimizing the individual safekeeping of your rooms, and ultimately helping the guards expel your unwanted intruder with little to no damage.
However, with today’s growing and expanding operational platforms and hybrid cloud environments, putting locks on each and every room of your Castle (Enterprise Data Center) quickly becomes impractical and unsustainable (traditionally done in a manual fashion). Therefore, the “Putting Locks on Every Room” approach drives the need to establish automation. An automated enterprise identity broker (your quartermaster) that issues keys only to the rooms of known good actors who are then granted access is the “trust nothing and authenticate and authorize everything” approach, and is the fundamental principle of Zero Trust. Establishing and managing identity is complex, so we are not finished with securing our Castle.
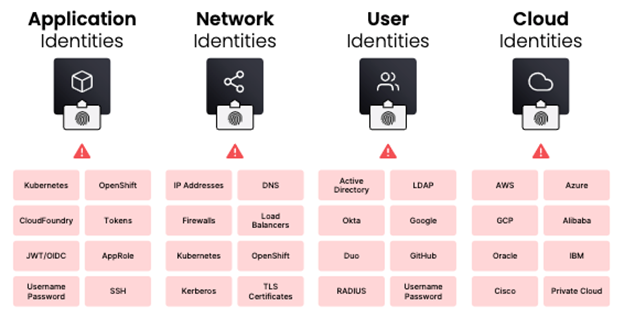
The challenge remains that all of this happens in the digital world at an exponentially high pace. In the hybrid cloud, dynamic or ephemeral services can and will spin up and down faster than any human can manage. This, combined with the need to maintain connectivity, requires extreme automation of the quartermaster position. Effectively, this approach will establish and provide a service mesh (secure by design) to users and machines alike, and all the secure ephemerality required.
Solution: Service Mesh 101 – Establishing Secure Service Connectivity and Preventing Lateral Movement
Applications in modern CI/CD workflows are being delivered by deploying code rapidly (often thousands of times a day) on many different runtimes and platforms. The complexity quickly becomes unmanageable, unless you can abstract and automate most of this complexity away and limit the cognitive load while maintaining security. We recommend that any organization venturing into the multi-cloud (C2E) and/or hybrid-cloud arena invest in a Service Mesh solution that allows both existing (current applications/services) and dynamic and ephemeral services to securely spin up and down as consumers and missions require. And, no, this is not beyond your organization’s capabilities
With the rising use of microservices, Kubernetes, public cloud, and hybrid computing, Site Reliability Engineers (SRE) and DevOps engineers are encouraged to avoid hardcoding values into application code and are also quickly adopting the much more secure approach of dynamic credentials (credentials/secrets generated on demand, with short TTL’s). Additionally, they have to ensure secure, resilient, and performant applications while reducing complexity at scale.
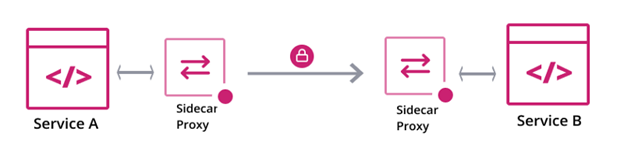
Image Source: (HashiCorp)
The adoption of a Service Mesh addresses the secure service connectivity issue across any platform and operational environment while simultaneously enabling identity driven, dynamic, secure connectivity while preventing unauthorized lateral movement. Fundamentally, a service mesh is a dedicated network layer that provides secure service-to-service communication within and across infrastructure, including on-premises and cloud environments. Service meshes are often used with a microservice architectural pattern, but can provide value in any scenario where complex networking is involved.
How does HashiCorp help?
Consul, HashiCorp’s Service Mesh solution, enables practitioners to achieve this today by leveraging secure service connectivity (using mTLS) between microservices in the mesh. Establishing identity based approaches for services (machines) is key to enabling secure service connectivity and preventing lateral movement.
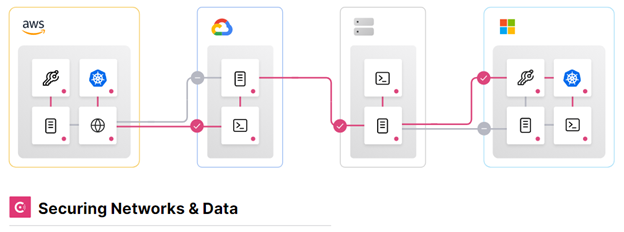
Consul allows platform teams to manage hybrid/multi-cloud networks by discovering and securely connecting services (based on identity) across most any operational platform. Consul provides a platform agnostic distributed service mesh that pushes routing, authorization, and other networking functions to the endpoints in the network. This makes the network topology simpler and easier to manage, reduces the need for expensive middleware devices within east-west traffic paths, and makes service-to-service communication more secure, reliable and scalable.
Zero Trust Networking with Service Mesh
- Machine-to-Machine Access: HashiCorp Consul enables machine-to-machine (service level) access by enforcing identity based authentication between applications and ensuring only the right machines are talking to each other (no lateral movement).
Furthermore, certificates, keys, and sensitive items and secrets in the mesh also need to be secured and managed. HashiCorp Vault helps practitioners simplify these workloads and centralize and protect these secrets across any operational platform. Vault’s Secrets engines provide infrastructure automation and are essential to reduce cognitive load for the teams trying to manage secrets. An example of some of the secrets found in service meshes are:
- Access control list (ACL) bootstrap token
- ACL partition token
- ACL replication token
- Enterprise license
- Gossip encryption key
- Snapshot Agent Config
- Server TLS credentials
- Service Mesh Client TLS credentials
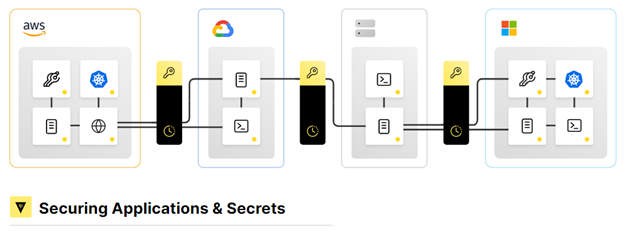
Centralization and protection of secrets across your environments are essential to stop a lateral attack among other vulnerabilities. Identity is the new perimeter and identity is a secret.
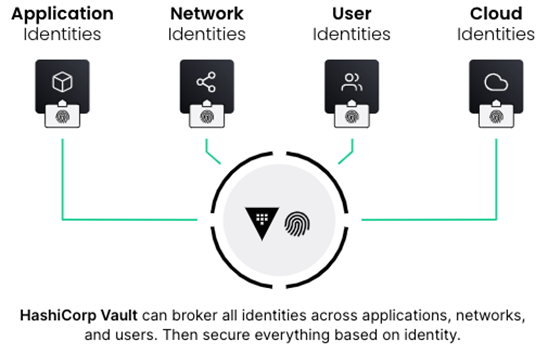
A service mesh can contribute to the problem of secret sprawl if not properly addressed. If you’re using, or planning to use, a service mesh you should consider the level of effort to store the secrets associated and learn how HashiCorp solutions can help secure and ease the cognitive load while defending against emerging threats. Follow the Vault as Secrets Management for Consul to learn how to start defending against lateral movement.
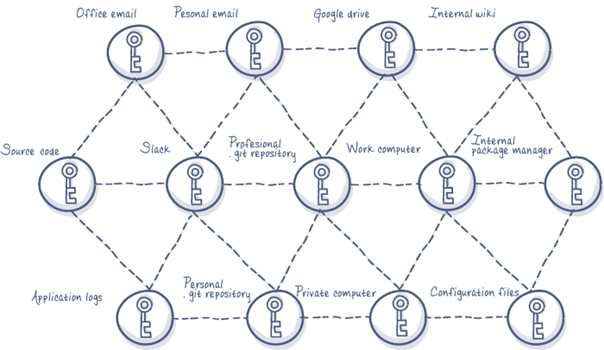
How HashiCorp can Help Prevent Lateral Movement with Vault and Consul
HashiCorp Vault (a secrets management platform) and HashiCorp Consul (a service mesh) are two good examples of integrating tools that can prevent lateral movement based on the MITRE ATT&CK Framework techniques. You can test this out and learn more at HashiCorp Developer.
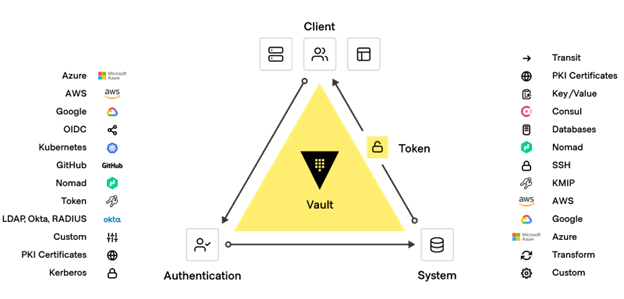
The Universal Principles of Zero Trust are designed into Vault – advanced security capabilities do not need to be bolted on.
For increased security, Consul can be integrated with Vault for centralized secrets management including PKI and certificate management with dynamic certificates and automatic certificate rotation on both the control plane and data plane. Consul Federated Service Mesh secures service connections across any hybrid cloud environment and on any runtime.
Conclusion
HashiCorp is secure platform automation for the hybrid/multi-cloud era. Many organizations implement this foundational approach to address some key use cases/workflows:
- Support Teleworking
- Protect Critical Resources
- Reduce Vulnerabilities and Threats
- Limit Exposure & Lateral Movement
- Improve Incident Response/Recovery
- Protect Sensitive Data
- Improve Visibility
Implementing a service mesh (identity based, secure service connectivity by design) with centralized secrets management and establishing core zero trust workflows addresses the issue of lateral movement and is often the foundational step for more advanced workflows, securing automated deployments, and accelerating secure mission deployments.
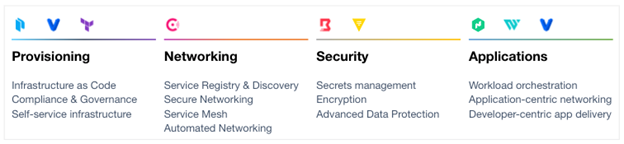
The HashiCorp suite of tools seeks to provide solutions for each layer of the cloud operating model and solve complex infrastructure challenges to meet mission needs. HashiCorp and our cloud infrastructure automation tooling are purposefully built to help complex organizations successfully deliver mission outcomes, securely, and at scale across any platform.
Additional Information:
White paper: Unlocking the Cloud Operating Model
White paper: Unlocking the Cloud Operating Model: Security
White paper: A Leadership Guide to Multi-Cloud Success for the Intelligence Community
White paper: Enabling Zero Trust Security in the Public Sector
Intelligence Community News Articles by HashiCorp:
- The Multi-Cloud Era is Here
- Getting Started with Zero Trust Security
- Enabling Zero Trust at the Application Layer
- Enabling Zero Trust at the Device/Machine and Human/User Layers
- A Leadership Guide – Multi-Cloud Success for the Intelligence Community
- A Practitioner’s Guide – Hybrid/Multi-Cloud Adoption for the Intelligence Community
- A Security Guide – Hybrid/Multi-Cloud Security for the Intelligence Community
- Just Start! – Implementing Zero Trust Workflows for the Intelligence Community
About HashiCorp
HashiCorp is the leader in multi-cloud infrastructure automation software. The HashiCorp software suite enables organizations to adopt consistent workflows to provision, secure, connect, and run any infrastructure for any application. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, and Nomad are downloaded tens of millions of times each year and are broadly adopted by the Global 2000. Enterprise versions of these products enhance the open source tools with features that promote collaboration, operations, governance, and multi-data center functionality. The company is headquartered in San Francisco and backed by Mayfield, GGV Capital, Redpoint Ventures, True Ventures, IVP, and Bessemer Venture Partners. For more information, visit www.hashicorp.com or follow HashiCorp on Twitter @HashiCorp.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.