From IC Insider Red Hat
Becoming quantum-ready is “imperative across all sectors of the United States economy, from government to critical infrastructure, commercial services to cloud providers, and everywhere else that vulnerable public-key cryptography is used.”
As the world’s leading provider of enterprise ready open source software, Red Hat must guide the way in providing solutions that help prepare the widely varying users of its embedded platform cryptography to protect and transition to a post-quantum world.
Experience the future of cybersecurity with Red Hat, the global leader in enterprise open source software. Our mission is to lead the way in providing innovative solutions that prepare users across various sectors for the impending quantum revolution.
Quantum Threat: A Present Challenge
Today, the danger of encrypted data falling into the wrong hands is real. Criminals and state actors are capturing sensitive information for future decryption and exploitation. Our current cryptographic systems, such as RSA, rely on prime factorization or other mathematical systems, which can be compromised by quantum computers. The implications for our trust in compute platforms, software distribution, data security, and telecommunications are immense.
All types of information systems are vulnerable – even ones that aren’t normally thought of as using cryptography actually do in ways that aren’t direct or obvious to end users but would be attackers armed with a Cryptographically Relevant Quantum Computer (CRQC). At stake are:
- The trustworthiness of our compute platforms: hardware roots of trust depend on Secure Boot, TPMs, FIDO, and a host of cryptographically protected mechanisms to make sure data isn’t stolen by attackers getting ‘under the hood’. – IoT devices running factories or collecting data from the field may be 25 yrs or more
- How we get software: software distribution (include web based services) and signing systems give us trust to run and use these tools – note that Microsoft’s root signing key is now 25 yrs old
- Our data and our identities that are bound to it: property, health, financial records, cryptocurrency, all depend on electronic record and transfer systems – remember your passport and its embedded RFID is good for 10 yrs
- Telecommunications and online services: these form our daily fabric of web sites, e-commerce, social media, cell phones and 5G – remember how long your social media profile lasts: Facebook has been around for 20 yrs
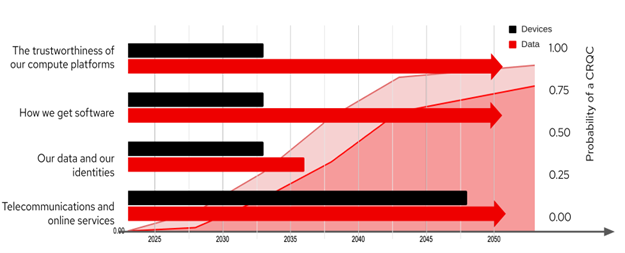
The timeframes for cryptography usage are already overlapping with the probable timeframes for probable introduction of CRQCs.
Embrace Post-Quantum Cryptography
The world needs to replace vulnerable cryptosystems with post-quantum alternatives. Red Hat recognizes the urgency and is already working with leading organizations like NIST and IBM to standardize and implement post-quantum encryption. Unlike the powerful quantum computers still in development, post-quantum cryptography is available now. By adopting these solutions, you can protect your data from current and future threats.
“Determining where migration to post-quantum cryptography will be required involves certain initial discovery steps for the development of migration roadmaps. These include the identification of affected standards by standards developing organizations (SDOs) and consortia, and the identification of critical applications and protocols on both an enterprise and sector-wide basis” – NIST
Red Hat: Your Trusted Partner
This open source community is building and testing candidate implementations of the NIST finalist algorithms to evaluate the drop-in suitability of the implementations for existing cryptosystems like RSA or ECDSA, as well as assessing performance and other characteristics of these implementations to both improve the implementations and measure potential impacts to dependent systems. As a trusted enterprise and platform provider, Red Hat has a long history of helping organizations adopt cutting-edge technologies. We are already updating adjacent standards and technologies and preparing our next-generation operating system and layered platforms to offer post-quantum cryptography. With Red Hat, you can navigate the complex transition to a quantum-ready world seamlessly and securely.
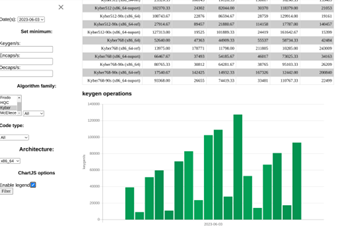
The open source community – openquantumsafe.org – is already testing and evaluating the performance of PQC alternatives
Addressing the Challenges Ahead
The migration to post-quantum cryptography is a monumental task that requires meticulous planning and execution. Red Hat is focused on tackling the main challenges head-on (noted below) because it will touch every aspect of how IT is built today. We are collaborating with industry leaders, supporting open-source communities, and building tools to manage and utilize post-quantum providers on our platforms. As with similar revolutions in IT over the last few decades – Y2K, web technologies, cloud adoption, and others – targeted solutions to address specific concerns at each phase of the migration cycle ahead will be critical.
- Challenge 1: NIST is still not ready to finalize algorithms and systems based on these. Early adopters must therefore be prepared to restart migrations or revert migrations mid-stream. Early solutions may need to focus on crypto agility to reduce the time required to transition to alternatives and to allow for seamless updates for future cryptographic standards should the need occur.
- Challenge 2: modern IT is central to virtually all aspects of companies, industries, and missions. The sprawl of IT creates the inherent challenge of the scale of executing a transition that will require us to operate in mixed and hybrid cryptographic enterprises for some time. We’ll need to automate the assessment and evaluation process to drive priorities with data and evidence, and to execute migrations of individual systems.
- Challenge 3: Continuing to operate enterprises and business systems and missions during this disruptive process. Minimizing the operational risk and impact to systems is essential to prevent modernization from stalling or stopping altogether. Early solutions that can layer over existing ICT and work with existing protocols in mixed deployments will be needed, as well as specialized tools to test, validate, measure performance, cost, scale, and overall impacts of these new cryptosystems to enterprise systems
Join the Quantum Revolution with Red Hat
Partnering with IBM and organizations like QuSecure, Red Hat is building a community to push the boundaries and advance the enterprise approach for quantum-ready technology. The goal is to extend our existing validated solutions that protect your data streams today while preparing you for the future.
Red Hat’s platform SMEs have worked with the QuSecure team to build on proven Red Hat platforms including RHEL, Openshift, and Ansible, allowing users to build off trusted Red Hat platforms and deploy their solutions with and into enterprises already using the leading open source enterprise technologies provided by Red Hat. By decoupling encryption layers and leveraging our trusted platforms, you can adapt seamlessly to post-quantum cryptography without disrupting your existing systems.
Don’t wait for quantum threats to compromise your security. Choose Red Hat and embark on the journey towards a quantum-ready world today. Talk to some of the experts at Red Hat about the use of cryptography in your enterprise and Red Hat estate today – and learn how you can start down a migration path today.
Contact Red Hat today to learn more about the state of post quantum cryptography standards and the tools that help you experiment with these emerging standards today, identify your high value systems that depend on cryptography, and start prioritizing and planning for your own enterprise transition. Visit ? red.ht/icn to learn more.
About Red Hat
Red Hat is the world’s leading provider of enterprise open source software solutions, using a community-powered approach to deliver reliable and high-performing Linux, hybrid cloud, container, and Kubernetes technologies. Red Hat helps customers develop cloud-native applications, integrate existing and new IT applications, and automate and manage complex environments. A trusted adviser to the Fortune 500, Red Hat provides award-winning support, training, and consulting services that bring the benefits of open innovation to any industry. Red Hat is a connective hub in a global network of enterprises, partners, and communities, helping organizations grow, transform, and prepare for the digital future.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.









