From IC Insider Siren
By John Randles, CEO of Siren
Cybersecurity threats represent the single greatest menace to governments and organizations today. To an extent this threat has been magnified due to COVID-19, as more of us are working from home on less stringent network environments. An organization’s ability to protect its data from its adversaries is critical to their survival. It takes little imagination to consider the catastrophic effect of a nation losing their passcodes to their enemy during a conflict. News media headlines are riddled with stories from data breaches to hostile malware – often orchestrated by state-sponsored nefarious organizations. As institutions struggle to fight these never-ending attacks, they must seek ways to mitigate and address these threats. An active cyber defense is often addressed by:
- Continuous improvement and adaptation
- Unique analytic capabilities
- Investigative tools
- Tailored agile cyber threat intelligence.
The Pyramid of Pain
Organizations address these threats through the Pyramid of Pain, a maturity model that spans from simple, frequent attacks against vulnerable endpoints through sophisticated attacks. As security analysts move from the bottom to the top of the Pyramid, their job becomes progressively more difficult. For example, while endpoint protection is the most frequent point of attack, it represents the lowest level of sophistication.
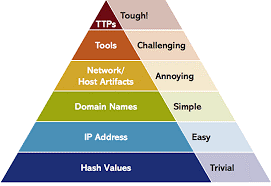
However, the most difficult levels for most organizations remain the top three categories. More importantly, these three categories require organizations to hire and retain security analysts with specific skill sets that need to be continuously sharpened and honed. Organizations must be able to uniquely adapt to different types of threats that are seen and observed or respond to an incident that may have been missed.
In addition to maintaining highly skilled individuals, organizations must be able to develop a tailored process and incorporate their own specific datasets. Indicators needed to be analyzed are often hidden across various system logs. For example, a hotel chain might have a rewards program that is subject to a fraud ring. The fraud may be a larger effort to hide more egregious behavior such as credit card theft or identity theft of their top-level clientele.
Incident Response
When compromise events occur, analysts must be able to update threat observables in real-time, visually updating the scope as new indicators are added to the intrusion set: enabling scalable collaboration, real-time situational awareness, and clear communication.
Historically, organizations have turned their attention to a Security Information and Event Management (SIEM) tool to solve these challenges. However, there are complementary technologies such as Siren to aid the Threat Analytics phase of problem solving. This tool empowers organizations to effectively deploy an enterprise-wide cyber threat intelligence and threat hunting capability.
Security analysts find themselves copying and pasting specific alerts or IPs and try to pivot through different dashboards and various search functions – ending up creating long, complex search queries. These end up being difficult to repeat and maintain. Siren enables analysts to search all the data in a single pane of glass, moving from one index to another through intuitive graphs or relational navigators – without complex query languages. The solution rapidly ingests any kind of telemetry data analysts want to throw at it.
Link Analysis with the Network Graph
Security analysts fall victim to eye and mental fatigue searching and manipulating the data. Through Siren’s Knowledge Graph, analysts are able to quickly expand, investigate, and drive insights in an intuitive link and node user interface. Imagine starting an investigation by graphing adversary behaviour and discovering a specific malware sample and its relationship to different infrastructures or mechanisms of operations – in the form of a picture. No logs. No endless commands. A clear, easy-to-understand network graph. In addition, through Siren’s Web Services, analysts can enrich their data on-the-fly. The knowledge graph can bring together, for example, OSINT sources, IDS alerts, CVE Data, Mitre Attack classification etc. to bring as much data as possible to bear on a particular threat.
Threat Hunting
Threat hunting comes down to being able to understand more discreet, nuanced behaviours observed on the network and associating them to discovered indications of an adversary.
Siren’s flexible data model allows security analysts to rapidly ingest discreet datasets on the fly and extend Siren’s existing data model without impacting other analysts’ work. With Siren’s data model, you’re not constrained to a specific set of indicators to start an investigation from certain classes of logs that you might use to scope. When the security analyst build’s the data model, he or she can effectively explore a living presentation of the data, no matter where the investigation starts.
Should I Ascend the Pyramid?
To answer this question , there are seven questions every Chief Information Security Officer should ask themselves:
- Do I really need to be at the “Top of the Pyramid” – Threat Hunting?
- Are advanced adversaries likely to overcome my automated cyber defence?
- Does my organisation make more than $300M/year?
- Do we work with PII or other valuable data?
- Do we work in a sensitive sector or have sensitive customers?
- Do we expect a targeted attack?
- Do we expect personalized malware?
Siren’s Security Analytics solution offers a full breadth of capabilities security professionals demand when working at the ‘Top of the Pyramid’.
Regardless of your environment, Siren offers several different integration options. Siren quickly leverages Elasticsearch and integrates with most SQL databases, datalakes and Siems such as Splunk. Siren holds a rich set of capabilities and a wide spectrum of hooks that can seamlessly integrate into any organizations’ framework. The intuitive user interface provides a rapid time-to-value for any security analyst.
Indicator Feeds, Telemetry Events, and Alerts
As security analysts work to understand how to make sense of their logs, they often copy and paste values from one point solution into another. Through the use of Siren’s Set to Set Navigation, analysts seamlessly pivot from one dashboard into another, giving them a powerful context navigation tool that makes exploring logs effortless. Switching between network segments provides analysts complete insight into logs that were once difficult to search and impossible to manage. For example, if an analyst receives an alert on Network A, they can quickly understand the relationship between that source and the destination alert, and other log sources that have traffic related to the nodes they are investigating.
With Siren, moving from one dashboard to another does not require any special search syntax or special search language to master. While this challenge may seem trivial, it plagues most security analysts today.
In Summary
Siren offers a spectrum of capabilities that fully support cyber threat hunting. From exploring adversaries attempting to breach networks to creative account takeover attempts, Siren’s robust data model and a rich library of visualizations make it a perfect extension to any Security Operation Center’s portfolio of solutions.
About Siren
Siren provides the leading Investigative Intelligence platform to some of the world’s largest and most complex organizations for Investigative Intelligence on their data. Rooted in academic R&D in information retrieval, distributed computing and knowledge representation, the Siren platform provides integrated investigative intelligence combining previously disconnected capability of search, business intelligence, link analysis and big data operational logging and alerting.
Among Siren awards are Technology Innovation of the Year and the Irish Startup of the Year (Ireland’s National Tech Excellence awards). In 2020, Siren was named as a Gartner Cool Vendor in an Analytics and Data Science Report. For more information, visit www.siren.io.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.









