From IC Insider HashiCorp
Back in 1996, a Microsoft employee developed the Point-to-Point Tunneling Protocol (PPTP). According to Techtarget, “The protocol created a more secure private connection between a user device and the internet.” Since then, virtual private networks (VPNs) have been the most secure solution for user access. Like most technologies, something better comes along to replace or augment mainstream tooling.
First, privileged access management (PAM) tools and jump hosts/bastion hosts existed. We’ve now moved beyond those tools, built in the age of the castle-and-moat datacenter and firewall, because we must evolve to support complex hybrid and multi-cloud environments against modern cybersecurity threats.
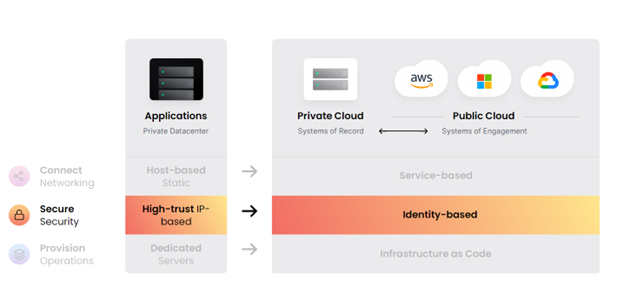
With the emergence of a multi-cloud reality and ephemeral infrastructure, enterprises, governments, and developers have a significant need for an Identity Aware Proxy (IAP). They need a consistent workflow and control point that allows users to access systems without the need to know specific credentials or public Internet Protocol (IP) addresses.
Organizations will still use VPNs and SSH keys, as with most technology shifts, but a few early adopters have already shifted to IAP.
In a traditional data center, a clear network perimeter and firewalls define an inside and outside. There is no “inside” or “outside” concept with an IAP. An IAP is a new, improved, modernized approach to traditional PAM. An IAP satisfies the same requirements as a traditional PAM but offers identity awareness versus a network-centric approach.
This approach is different from other software. These design principles are based on the trust nothing, authenticate everything premise. Moving from high-trust to low-trust environments, the resource becomes the focus, not the network. While traditional PAM solutions can only provide secure access on a limited basis through the network, a modern IAP solution provides secure remote access to any infrastructure service through identity. This concept can be described as privileged resource management.
Design Principles
An effective identity-aware solution includes capabilities such as dynamic infrastructure access, fine-grained control, context-aware decision-making, strong TLS management, and adherence to Zero Trust principles. It must also be a scalable and secure solution for managing access to dynamic infrastructure.
Scaling
Today’s IAP solutions should be designed to scale effortlessly, accommodating individual users and enterprises. Unlike many products that rely on cloud vendors and services with varied pricing, a well-designed IAP takes a different approach. Recognizing the complexities enterprise customers face, often operating in multi-cloud and on-premises environments with various geopolitical and contractual obligations, Boundary ensures flexibility by providing the ability to run anywhere.
Scaling is a core part of the system designs which applies to requests-per-second-style scaling and organizational scaling. This scalability principle empowers users to access and secure their networks regardless of their infrastructure choices.
Security
Security is a top priority in Boundary’s design, drawing inspiration from an enterprise or global identity and secrets management system. The emphasis on accessible, best-practice security measures ensures that user data remains protected.
TLS management
As a solution, IAP leverages modern security measures, such as authenticated Transport Layer Security (TLS) stacks, to protect connections between its components. TLS 1.3, the latest protocol used for secure communication, offers enhanced security, improved performance, perfect forward secrecy (PFS), streamlined resumption of previous sessions, and the removal of legacy and insecure features. By leveraging TLS 1.3, an IAP solution should also ensure robust encryption, faster connections, and increased protection against attacks, making it a reliable choice for secure network access management.
Zero Trust (KMS and RBAC)
To establish a secure root of trust, an IAP can employ key-management systems located in the physical data center or the cloud. Operators can then encrypt sensitive values using passwords or API keys to enable secure workflows. This encrypted information can be safely stored and transmitted across various systems, ensuring secure access to sensitive data throughout the workflow.
IAP solutions should also implement role-based access controls (RBACs) that apply to all resources within the system. This means that permissions would not be granted by default, but instead explicitly assigned based on the principle of least privilege. This approach reduces the cognitive load for users, prevents accidental granting of excessive privilege, and maintains a high level of security, ensuring fine-grained control. Access is explicitly granted in a zero-trust posture, including access for anonymous users, eliminating any implicit trust and ensuring that all users adhere to very precise access control mechanisms.
Core Architecture Overview
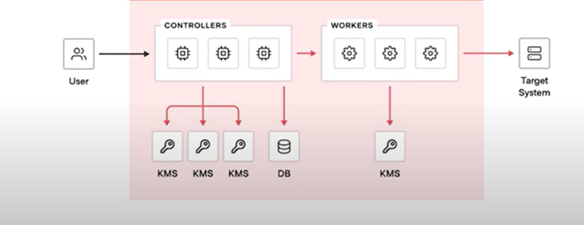
A nominal core IAP architecture consists of a control plane and a data plane. Each has specific components that work together to deliver its functionality. Let’s explore these components in more detail.
Nominal Core Architecture
Control Plane
The control plane is responsible for managing and coordinating the overall operation of the solution, consisting of the following components:
Controllers form the system’s backbone and implement the domain model. They would handle authentication and authorization and serve API requests. Controllers could be designed to be leaderless, enabling predictable horizontal scaling and fault tolerance. This architecture ensures the solution can handle high loads and maintain availability even in complex environments.
Key-Management Systems (KMSs) are crucial in establishing a secure root of trust within the IAP. They provide the necessary cryptographic mechanisms for secure communication between components and protecting sensitive information such as TLS credentials.
Relational Databases provide persistence and storage of the domain model. They store essential data such as user information, session details, targets, credentials, etc. Using a relational database enables the IAP to ensure data accuracy, consistency, and efficient retrieval when handling complex queries or authorization requests.
Data Plane
The data plane focuses on the execution of network sessions and includes a mechanism known as a worker.
Workers are responsible for proxying sessions. They handle the actual data transmission between authorized users and target systems. By separating the session handling from the control plane, Boundary achieves a modular architecture that allows efficient resource utilization and scaling based on workload demands.
Gain Visibility and Insights to Access Patterns
A data warehouse can truly differentiate IAP solutions. The data warehouse can uncover valuable insights, including session facts, connection details, user and host dimensions, and timestamps.
Imagine using popular business intelligence tools like Tableau to delve into host access patterns, revealing anomalies and uncovering potential data exfiltration. A solution that leverages a data warehouse can be pre-built, eliminating the need for complex ETL processes or designing your own. An integrated data warehouse provides extensive visibility into network access environments.
Conclusion
An identity aware proxy introduces privileged resource management as the new approach to traditional privileged access management. It couples identity and secrets management with remote access, using tools such as HashiCorp Vault and Boundary, to modernize and secure remote access workflows. As we have stated, there is no concept of an “inside” or “outside” with this new approach.
To learn more about HashiCorp Boundary, visit www.hashicorp.com/products/boundary. Boundary satisfies the requirements found in traditional privileged access management but also offers identity awareness via identity-based privileged resource management.
To learn more about HashICorp Vault, visit www.hashicorp.com/products/vault. Vault is the centerpiece of a zero trust architecture, delivering centralized identity and secrets management across the entire enterprise.
About HashiCorp
HashiCorp is the leader in multi-cloud infrastructure automation software. The HashiCorp software suite enables organizations to adopt consistent workflows to provision, secure, connect, and run any infrastructure for any application. HashiCorp open source tools Vagrant, Packer, Terraform, Vault, Consul, and Nomad are downloaded tens of millions of times each year and are broadly adopted by the Global 2000. Enterprise versions of these products enhance the open source tools with features that promote collaboration, operations, governance, and multi-data center functionality. The company is headquartered in San Francisco and backed by Mayfield, GGV Capital, Redpoint Ventures, True Ventures, IVP, and Bessemer Venture Partners. For more information, visit www.hashicorp.com or follow HashiCorp on Twitter @HashiCorp.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.









