HashiCorp’s Infrastructure and Security Lifecycle Management and The NSA’s Top Ten Cloud Security Mitigation Strategies

From IC Insider HashiCorp
By: Greg Thomas, Timothy J. Olson, Timothy Silk
The Intelligence Community (IC) is moving from a single-cloud community to a multi-cloud community with the introduction of the Commercial Cloud Enterprise (C2E) contract. With a broader availability of Cloud Service Providers (CSPs), many users in the IC are becoming smarter and more discerning cloud consumers.
Multi-cloud brings many significant challenges, the most impactful is security. The National Security Agency has published “Top Ten Cloud Security Mitigation Strategies” to help cloud customers adapt to the paradigm shift. The full list of the ten strategies is covered in detail in the following reports:
- Uphold the cloud shared responsibility model
- Use secure cloud identity and access management practices (Joint with CISA)
- Use secure cloud key management practices (Joint with CISA)
- Implement network segmentation and encryption in cloud environments (Joint with CISA)
- Secure data in the cloud (Joint with CISA)
- Defending continuous integration/continuous delivery environments (Joint with CISA)
- Enforce secure automated deployment practices through infrastructure as code
- Account for complexities introduced by hybrid cloud and multi-cloud environments
- Mitigate risks from managed service providers in cloud environments (Joint with CISA)
- Manage cloud logs for effective threat hunting
In this article, we will provide a high level overview where HashiCorp solutions address and align with the strategies listed above.
Introduction
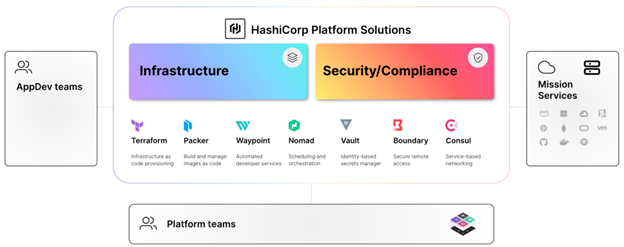
HashiCorp is a leader in multi-cloud infrastructure automation software (A Leadership Guide to Multi-Cloud Success for the Intelligence Community). The HashiCorp software suite enables organizations to adopt consistent workflows (Unified Interface) and a standardized approach to automating the critical process involved in delivering applications securely in the cloud. The C2E transition means there is now an opportunity to take a broader view of CSPs and enable, standardize, and apply key elements of the Top 10 Cloud Security Mitigation Strategies (Top 10) across all environments by adopting HashiCorp solutions.
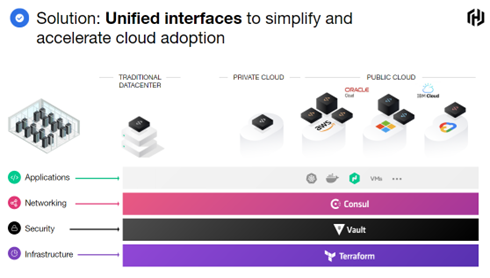
Establishing a platform approach is instrumental in achieving the maximum benefits from hybrid/multi-cloud environments and key from a security perspective. Effective platform teams deliver shared infrastructure, runtimes, services, and standardized workflows, enabling secure operational cloud adoption and implementation of the Top 10 strategies.
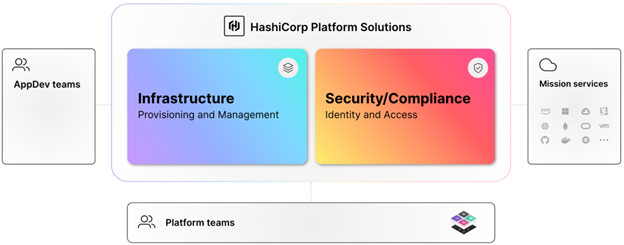
Adoption of these practices establishes platform services across the hybrid/multi-cloud environment and presents a standardized approach to apply key elements of the Top 10 strategies using an industrialized process for secure application delivery, all while taking advantage of the dynamic nature of each layer of the cloud. The platform team’s responsibility is life cycle management of infrastructure and security, to keep the platform stable, resilient, performant, and secure.
For hybrid/multi-cloud computing to be effective and adaptable for mission deployments, there needs to be consistent, secure approaches and workflows that are reused at scale across multiple environments and cloud providers. HashiCorp’s vision and solution offerings as a leading infrastructure automation company enable and address the Top 10 strategies as listed in the table below:
Manage secrets and implement advanced data protection and encryption everywhere
HashiCorp Vault Enterprise enables organizations to manage secrets, protect sensitive data, and control access to conform to relevant compliance frameworks across operational platforms. It addresses and enables several of the Top 10 strategies. Vault Enterprise is identity-based and Zero Trust (ZTS) by design. Vault authenticates these identities and uses them as a system of record to manage and enforce access to secrets and systems across the hybrid/multi-cloud.
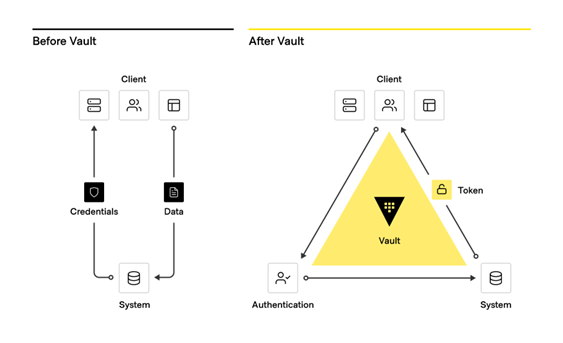
From traditional secrets workflow to modern secrets management with Vault
Vault Enterprise key capabilities:
- Manage secrets and protect sensitive data: Vault centrally stores, accesses, and deploys secrets across applications, systems, and platforms/infrastructure.
- Protect critical systems and customer data: Reduce the risk of breaches and data exposure with identity-based security automation and encrypting and securing application data (Encryption-as-a-Service) with one centralized workflow.
- Advanced auditing and reporting: Every operation with Vault is an API request/response and Vault audit logs contain every authenticated interaction.
Centralization versus decentralization of secrets
It’s just a matter of time before someone gains access to your network, behind your castle and moat. It happened in the Target breach, the Neiman Marcus breach, the Google breach, the Equifax breach, and the list goes on. From an offensive perspective, it is almost inevitable before an unmanaged secret is compromised.
Managed secrets are securely stored in a centralized platform so if a credential is compromised it can quickly be rotated or revoked. There are two main types of secrets:
- Dynamic secrets, generated on demand, as needed, and can be rotated with a lease
- Static secrets which commonly involve manual approaches to manage and rotate
The first step is to conduct periodic secret scans and create an environment where secrets are not long-lived but dynamic with predetermined leases. By leasing secrets, we effectively mitigate number six in the NSA’s Top Ten Cloud Security Mitigation Strategies.
Enabling Identity-based Security
Vault’s identity system is an essential capability that enables the brokering of identities between different platforms, establishing unified global identities and allowing applications to work across platform boundaries. Whether a machine or user needs to create and distribute organizational secrets, Vault manages this access based on trusted identities.
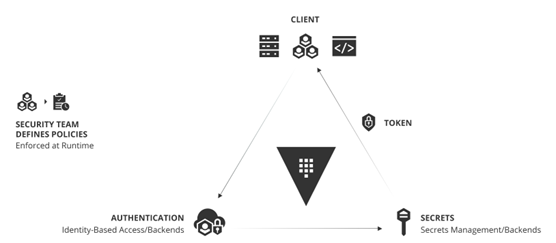
Operating Model for Identity-based Security and Secrets Management
The adoption of this operating model for identity-based security and secrets management with Vault is a critical shift for enterprises aiming to rationalize security in a world of hybrid/multi cloud and establishes the identity foundation that enables adoption of critical elements of the Top 10.
Dynamic Secrets, Key Management, and Encryption as a Service
Vault enables IC organizations to provide secrets management and data encryption services across platforms, applications, and mission teams. Overall security posture can be significantly increased using dynamic secrets in Vault. This will enable secrets to be created on demand and time-bound, greatly enhancing overall security posture and addressing key Top 10 items. Vault, as a central secrets manager, can revoke all secrets in the event of a breach or attack.
Vault Enterprise supports key management and is a crucial element of the Top 10. NIST Special Publication 800–63B goes into depth on digital identity guidelines, authentication, and lifecycle management. Vault Secrets Management solution is FIPS 140 compliant from the Enterprise to the Edge across hybrid/multi-cloud environments.
Vault can provide a central, standardized, encryption as a service (EaaS) as a consistent API for key management and cryptography. The Vault API exposes cryptographic operations to secure sensitive data without exposing encryption keys. Vault also can act as a certificate authority (root or intermediary) to provide dynamic short-lived certificates to secure communications with SSL/TLS.
Defending Continuous integration/continuous delivery environments
A unified security life-cycle management approach that provides central visibility and control across hybrid and remote environments is essential. Number six, defending continuous integration/continuous delivery environments calls for secrets discovery and management. A common challenge is the presence of fragmented solutions for secrets management that can only manage Active Directory, service accounts, or PAM secrets. The terrain is more complex now – a holistic approach with centralized Vault Enterprise secrets management addresses this Top 10 item.
Enforce secure automated deployment practices through Infrastructure as Code
HashiCorp Terraform Enterprise is an industry-leading infrastructure as code (IaC) solution and provides a consistent, automated workflow to manage hundreds of hybrid/multi-cloud resources and services. Terraform Enterprise allows organizations to ensure infrastructure platforms are built and managed in a compliant manner at scale, addressing key strategies in the Top 10.
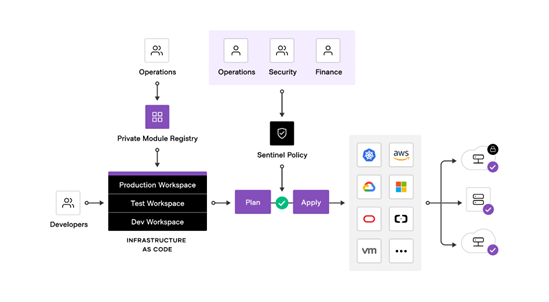
Terraform Enterprise addresses the seventh item of the Top 10, to Enforce automated deployment practices through infrastructure as code. This closely resembles the HashiCorp Terraform Security model. In addition, the risk posed by potentially unauthorized/unsupported software is the largest risk to the intelligence community as the old argument of the “eyes of many” falls apart with Sabotage in the Supply Chain.
Key features Terraform Enterprise provides to enable compliant infrastructure include and enable key elements of the Top 10:
- Infrastructure as code (IaC): Automate everything through code and maintain compliance with hardened modules ensuring provisioning of secured and standardized infrastructure.
- Policy as code (PaC): HashiCorp Sentinel creates and enforces policy as code, embedded in the workflow.
- Version control system (VCS) integration: Connections to major VCS providers allowing for automated management and running of configuration (IaC) and policy (PaC) files.
- Infrastructure state and drift management: State files provide a holistic view of current and previously configured versions of your infrastructure, enabling drift detection, compliance checks, and auditing.
Build consistent, compliant machine images for every environment
HashiCorp Packer allows for creation of identical, hardened machine images that are verified as compliant (Golden images) across multiple platforms from a single source configuration. These golden images enable rapid mission deployment across multiple platforms and address hardened requirements in the Top 10.
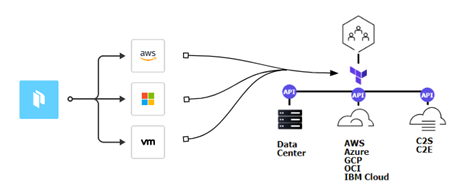
Compliant Automated Workflows – Adopting Policy as Code (PaC)
Policy as Code (PaC) is a key phase of compliant automation and key to enabling DevSecOps. It is an essential part of the Top 10. PaC limits exposure by codifying and enforcing policies to ensure infrastructure deployments are compliant. Together IaC and PaC empower organizations to rapidly and securely deploy any infrastructure platform for any application. HashiCorp’s Sentinel enables DevSecOps (Top 10 item) and provides embedded compliance and governance without requiring a shift in the overall team workflow.
Sentinel provides these key advantages when deploying secure platforms:
- Embedded: Enable policy enforcement in the workflow to reject active violations rather than after the fact inspection or passively detecting them.
- Multiple enforcement levels: Allow policy writers to warn or reject offending behavior.
- External information: Source external information to make holistic policy decisions.
- Hybrid/Multi-cloud compatible: Ensure infrastructure changes are within mission and regulatory policy across every infrastructure provider.
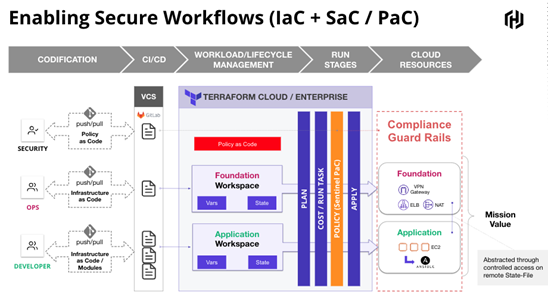
Adopting Auditing and Compliance
Establishing automation with built-in policy enforcement (compliance) and logging will accelerate auditing and compliance processes, automate and enforce policies, increase mission readiness, and enable key elements of the Top 10. HashiCorp solutions integrate with SIEM and SOAR tooling to help organizations build, maintain, and audit compliant infrastructure platforms across all layers of the cloud.
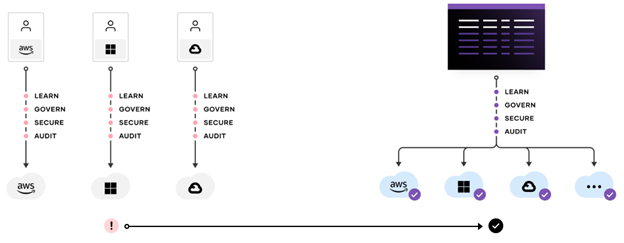
Secure service level connectivity (Application Level Networking)
HashiCorp Consul Enterprise is a secure service networking solution built for dynamic, hybrid cloud environments that is optimized to ensure secure networking best practices. Consul helps organizations discover and securely connect services running in any environment.
- Discover services: Consul is a dynamic service registry that can be leveraged as a single source of truth for any service running across all environments.
- Secure service networking: Discover and securely connect services and enable microsegmentation, all based on identity and intentions. Consul enables a “defense in depth” approach to implement a zero trust environment.
- Automated networking (Network Infrastructure Automation): Automate network processes using Consul-Terraform-Sync. Trigger automated network infrastructure updates using Terraform that can then be validated against Sentinel policies.
- Securely access services: Federated service mesh provides the means to manage and ensure secure, identity-based connectivity between services in an east-west pattern.
HashiCorp Consul enables platform teams to manage hybrid/multi-cloud networks by discovering and securely connecting services across almost any operational platform.
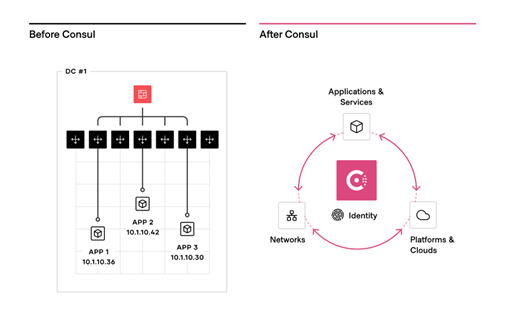
Zero Trust Networking with Service Mesh and API Gateway
Consul, HashiCorp’s Service Mesh solution, enables Top 10 strategies by leveraging secure service connectivity (using mTLS) between microservices in the mesh. Establishing identity-based approaches for services (machines) is key to enabling secure service connectivity and preventing lateral movement. Consul provides a platform-agnostic distributed service mesh that pushes routing, authorization, and other networking functions to the endpoints in the network.
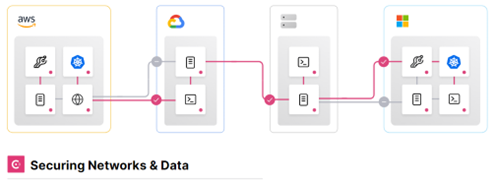
For increased security, Consul can be integrated with Vault for centralized PKI and certificate management with automatic certificate rotation on both the control plane and data plane. Consul Federated Service Mesh secures service connections across any hybrid cloud environment and on any runtime.
Identity-driven user access
HashiCorp Boundary solves modern access challenges and addresses another element of the Top 10. Boundary is a secure remote access solution that provides a straightforward approach to safeguard access to applications and critical systems with fine-grained authorizations based on trusted identities. Boundary governs access clouds, local datacenters, and low-trust networks, without exposing the underlying network.
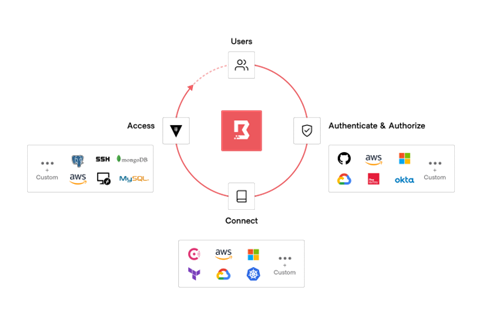
HashiCorp Boundary delivers simple and secure remote access to any
system anywhere, based on user identity
Users can authenticate to Boundary using their identity provider of choice and be tightly authorized to perform actions on a dynamic set of targets. Additionally, the user can be granted just-in-time access to connect to those targets via dynamic credentials provided by Vault.
Adopting Zero Trust Security
Enabling and adopting Zero Trust addresses foundational Top 10 needs. HashiCorp solutions are identity-based and Zero Trust by design and have outlined fundamental steps organizations can take to enable a zero trust approach and increase their zero trust security posture. For more information please refer to the White Paper: Enabling Zero Trust Security in the Public Sector.
Conclusion
HashiCorp provides secure platform automation for the hybrid/multi-cloud era. Adoption of secure, platform-agnostic, identity-driven solutions increases overall mission flexibility and effectiveness and helps future-proof and position for advancing technologies, enabling implementation of many of the key elements of the Top 10.
About IC Insiders
IC Insiders is a special sponsored feature that provides deep-dive analysis, interviews with IC leaders, perspective from industry experts, and more. Learn how your company can become an IC Insider.








