IARPA is gathering info for broad agency announcement on ‘Secure Multiparty Computations’
 The Intelligence Advanced Research Projects Activity (IARPA) has requested information from industry about better ways to develop tools that can help generate what the Intelligence Community calls “Secure Multiparty Computations.”
The Intelligence Advanced Research Projects Activity (IARPA) has requested information from industry about better ways to develop tools that can help generate what the Intelligence Community calls “Secure Multiparty Computations.”
“Secure Multiparty Computation (MPC) is a solution to the very general problem in which parties A, B, …want to compute a joint function f (a, b, …) on their respective inputs, but no party wants to reveal its input to any other party,” explains a Request for Information (RFI) issued by IARPA on February 10.
MPC protocols can be used for a variety of purposes, including (1) allowing a person or corporation to store and manipulate data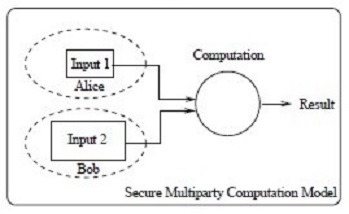 in an untrusted cloud computing infrastructure, as confidentially as if that data were stored in their own network; (2) allowing a Web server to customize the presentation of data based on a user’s identity, preferences, interests, or other private information, without learning that information; or (3) allowing a group of users to determine a course of action that is optimal for the group as a whole, without requiring any user to reveal which course of action they personally prefer.
in an untrusted cloud computing infrastructure, as confidentially as if that data were stored in their own network; (2) allowing a Web server to customize the presentation of data based on a user’s identity, preferences, interests, or other private information, without learning that information; or (3) allowing a group of users to determine a course of action that is optimal for the group as a whole, without requiring any user to reveal which course of action they personally prefer.
“The design of an MPC protocol for a specific application typically considers three main factors: a model of the available computation, an appropriate security threat model, and the specific computation to be performed,” explains the RFI.
IARPA is inviting parties with capabilities in this arena to respond to its RFI by March 31. The agency wants to receive submissions that discuss one or more of the following topics:
1. Formalization of Security and Privacy Constraints for MPC Protocols — especially identifying, formalizing and quantifying leakage so that all information flows are explicit.
2. Quantitative Metrics for Security, Privacy, and Efficiency of MPC Protocols – including the identification of sound metrics for measuring progress and ultimate success of automatic protocol generation tools.
3. Parameterized Families of MPC Protocols – discussing current research in MPC protocols that are already parameterized or can be parameterized.
4. Research Roadmap – including a discussion of the challenges in developing tools for automatic generation of provably secure MPC protocols, tailored to concrete application parameters, and proposing a research roadmap for getting to this end state.
IARPA wants to receive a one-page cover letter, a one page executive summary and up to five pages of discussion on one or more of the specified topics.
Further information is available from W. Konrad Vesey, the program manager, at dni-iarpa-rfi-14-03@iarpa.gov.








